New Phishing Attack Delivers Keylogger Disguised as Bank Payment Notice
A new phishing campaign has been observed leveraging a novel loader malware to deliver an information stealer and keylogger called Agent Tesla.
Trustwave SpiderLabs said it identified a phishing email bearing this attack chain on March 8, 2024. The message masquerades as a bank payment notification, urging the user to open an archive file attachment.
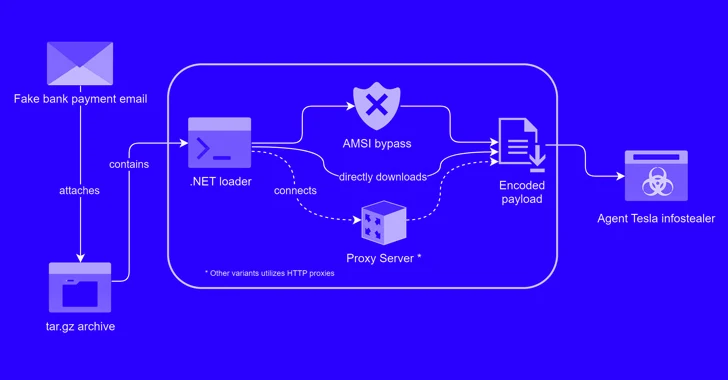
The archive (“Bank Handlowy w Warszawie – dowód wpłaty_pdf.tar.gz”) conceals a malicious loader that activates the procedure to deploy Agent Tesla on the compromised host.
“This loader then used obfuscation to evade detection and leveraged polymorphic behavior with complex decryption methods,” security researcher Bernard Bautista said in a Tuesday analysis.
“The loader also exhibited the capability to bypass antivirus defenses and retrieved its payload using specific URLs and user agents leveraging proxies to further obfuscate traffic.”
The tactic of embedding malware within seemingly benign files is a tactic that has been repeatedly employed by threat actors to trick unsuspecting victims into triggering the infection sequence.
The loader used in the attack is written in .NET, with Trustwave discovering two distinct variants that each make use of a different decryption routine to access its configuration and ultimately retrieve the XOR-encoded Agent Tesla payload from a remote server.
In an effort to evade detection, the loader is also designed to bypass the Windows Antimalware Scan Interface (AMSI), which offers the ability for security software to scan files, memory, and other data for threats.
It achieves this by “patching the AmsiScanBuffer function to evade malware scanning of in-memory content,” Bautista explained.
The last phase involves decoding and executing Agent Tesla in memory, allowing the threat actors to stealthily exfiltrate sensitive data via SMTP using a compromised email account associated with a legitimate security system supplier in Turkey (“merve@temikan[.]com[.]tr”).
The approach, Trustwave said, not only does not raise any red flags, but also affords a layer of anonymity that makes it harder to trace the attack back to the adversary, not to mention save…