Internet Computer blockchain has raised $80M | Dfinity Foundation
The Internet Computer Protocol is an ambitious blockchain project aimed at creating a world computer, and according to a new report from the shepherding nonprofit Dfinity Foundation, it has raised more than $80 million to date.
The Internet Computer Protocol (ICP) realizes the vision of a World Computer – an open and secure blockchain-based network that can host programs and data in the form of smart contracts, perform computations on smart contracts in a secure and trustworthy way, and scale infinitely.
Competing and coexisting with other blockchains like Bitcoin, Ethereum and Solana, the ICP has evolved into one of the first Bitcoin Layer-2s, with over $67 million in ckBTC (chain-key Bitcoin) transactions and 300-plus developers crafting Bitcoin-enabled decentralized apps (dApps).
“The ICP community has made tremendous strides this past year, from expanding the ICP Hubs Network globally to integrating Bitcoin at the protocol level directly on-chain to allow cryptocurrency to be used in everyday applications.” said Lomesh Dutta, vice president of growth at Dfinity Foundation. “The success of the SNS framework has been a big win for decentralized governance worldwide, and through its innovative tech stack and multiple network integrations, the ICP is unlocking access to a seamless, trustless multichain future for Web3.”
GB Event
GamesBeat Summit Call for Speakers
We’re thrilled to open our call for speakers to our flagship event, GamesBeat Summit 2024 hosted in Los Angeles, where we will explore the theme of “Resilience and Adaption”.
Dfinity Foundation role
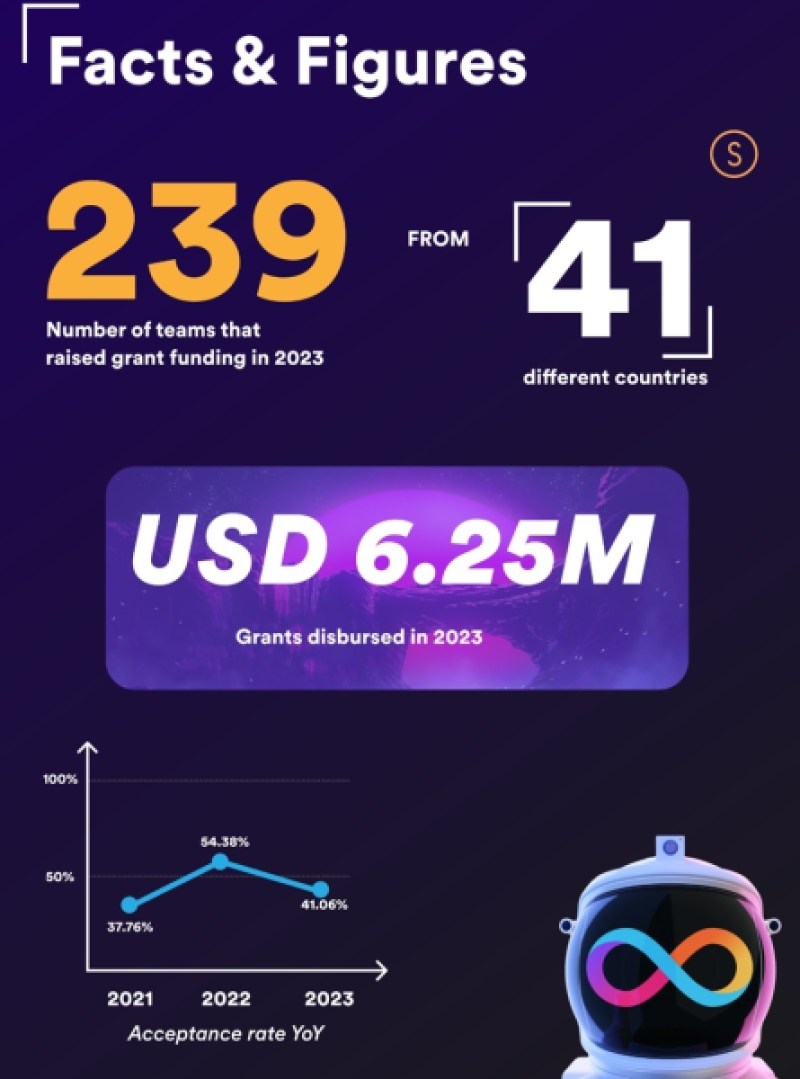
I spoke with Dutta about the significance of the report.
As vice president of growth at the Dfinity Foundation, Dutta’s team is the one responsible to essentially help all the teams that are building on…



