O.MG Elite Cable has power of a $20,000 hacking tool; can compromise iPhone, Android, Mac, PC
Shown off at this year’s Def Con is an unassuming and powerful hacking tool, the O.MG Elite cable. With the physical appearance of a standard Lightning or USB-C cable, the hidden modifications mean this cable can log keystrokes, perform attacks, and even transmit data stealthily from air-gapped devices with its own WiFi network.
Seen by The Verge‘s Corin Faife at Def Con, here’s how creator MG decribes the creation:
“It’s a cable that looks identical to the other cables you already have,” explains MG, the cable’s creator. “But inside each cable, I put an implant that’s got a web server, USB communications, and Wi-Fi access. So it plugs in, powers up, and you can connect to it.”
One of the powerful things about the new O.MG Elite compared to its predecessors is the advanced network features mean it can handle bidirectional communications.
O.MG Elite can perform attacks and read data that’s passed through the cable, say between iPhone and Mac, or almost any other combination of devices as it comes in Lightning to USB-A, Lightning to USB-C, C to C, and microUSB versions.
Creator MG says that up until now, a cable like this would have sold for as much as $20,000. But it’s going from $180+ to early access customers.
Attacks, keylogger, and built-in WiFi
O.MG Elite is able to carry out keystroke injection attacks – which makes a device think it’s a keyboard typing commands. That opens up vulnerabilites like command line attacks.
“It also contains a keylogger: if used to connect a keyboard to a host computer, the cable can record every keystroke that passes through it and save up to 650,000 key entries in its onboard storage for retrieval later. Your password? Logged. Bank account details? Logged. Bad draft tweets you didn’t want to send? Also logged.”
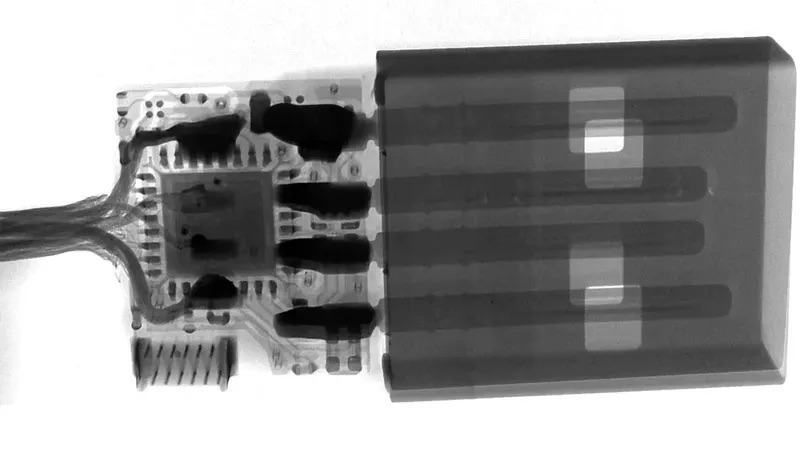
As noted by The Verge, a big part of how scarily capable this cable can be is the built-in WiFi to silently send back data to an attacker – even on air-gapped devices.
“Many ‘exfiltration’ attacks — like the Chrome password theft mentioned above — rely on sending data out over the target machine’s internet connection, which runs the…




