Sign1 malware campaign already infected 39,000 WordPress sites
Large-scale Sign1 malware campaign already infected 39,000+ WordPress sites
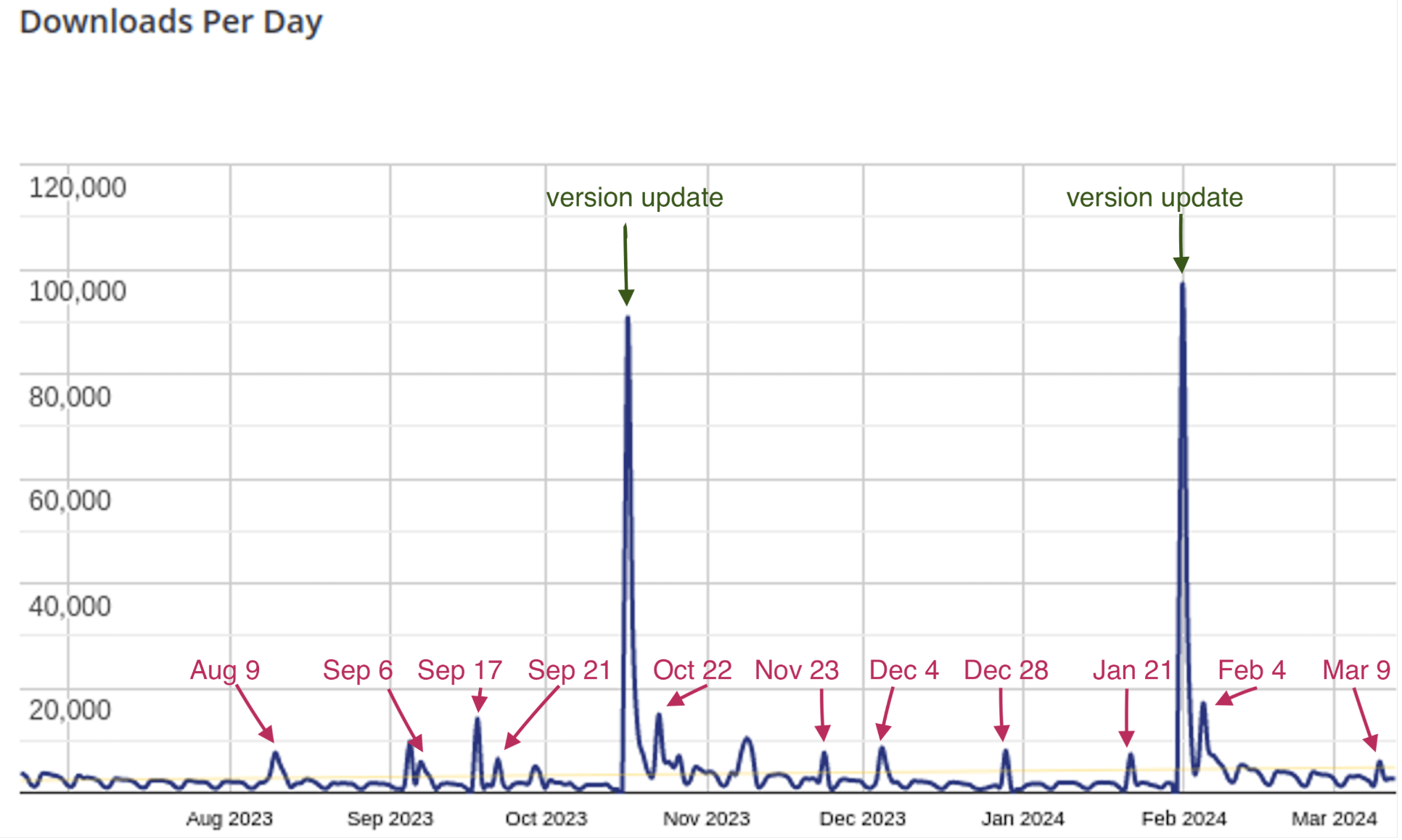
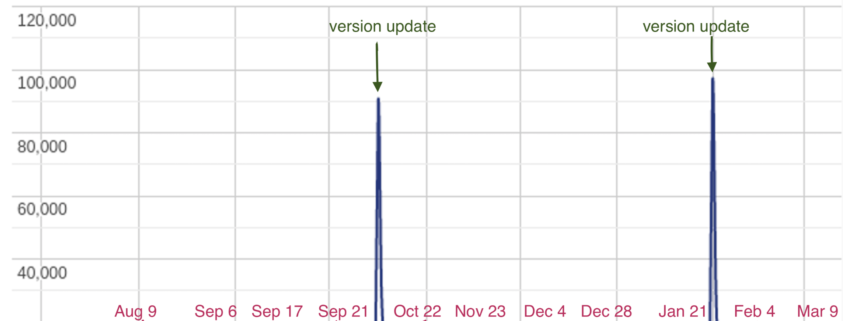
A large-scale malware campaign, tracked as Sign1, has already compromised 39,000 WordPress sites in the last six months.
Sucurity researchers at Sucuri spotted a malware campaign, tracked as Sign1, which has already compromised 39,000 WordPress sites in the last six months.
The experts discovered that threat actors compromised the websites implanting malicious JavaScript injections that redirect visitors to malicious websites.
Querying SiteCheck, the researchers discovered that the campaign infected over 2,500 sites in the past two months.
“Plugins that allow for arbitrary JavaScript and other code to be inserted into a website are especially useful for website owners and developers but can also be abused by attackers in a compromised environment. Since these types of plugins allow for pretty much any code at all to be added, attackers often use them to insert their malicious or spammy payload.” reads the report published by the experts. “Sure enough, checking the plugin settings revealed our culprit nestled inside Custom CSS & JS“
The threat actors behind Sign1 inject malicious JavaScript into legitimate plugins and HTML widgets. The injected code includes a hard-coded array of numbers that uses XOR encoding to get new values.
The experts decoded the XOR-encoded JavaScript code and discovered which it was used to execute a JavaScript file hosted on a remote server.
The researchers noticed that attackers employed dynamically changing URLs, the use of dynamic JavaScript code allows to change URLs every 10 minutes. The code is executed in the visitors’ browser, leading to unwanted redirects and ads for site visitors.
This code stands out because it checks whether the visitor came from a well-known website like Google, Facebook, Yahoo, or Instagram. If the visitor isn’t referred by one of these popular sites, the malicious code won’t run. Threat actors used this trick to avoid detection. Normally, someone who owns a website would visit it directly, instead of going through a search engine first. Malware uses this difference to try and stay…