Iran-Based Hackers Caught Carrying Out Destructive Attacks Under Ransomware Guise
The Iranian nation-state group known as MuddyWater has been observed carrying out destructive attacks on hybrid environments under the guise of a ransomware operation.
That’s according to new findings from the Microsoft Threat Intelligence team, which discovered the threat actor targeting both on-premises and cloud infrastructures in partnership with another emerging activity cluster dubbed DEV-1084.
“While the threat actors attempted to masquerade the activity as a standard ransomware campaign, the unrecoverable actions show destruction and disruption were the ultimate goals of the operation,” the tech giant revealed Friday.
MuddyWater is the name assigned to an Iran-based actor that the U.S. government has publicly connected to the country’s Ministry of Intelligence and Security (MOIS). It’s been known to be active since at least 2017.
It’s also tracked by the cybersecurity community under various names, including Boggy Serpens, Cobalt Ulster, Earth Vetala, ITG17, Mercury, Seedworm, Static Kitten, TEMP.Zagros, and Yellow Nix.
Attacks mounted by the group have primarily singled out Middle Eastern nations, with intrusions observed over the past year leveraging the Log4Shell flaw to breach Israeli entities.
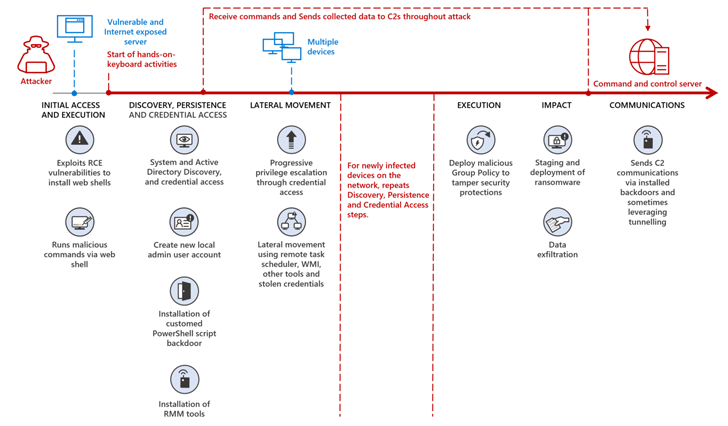
The latest findings from Microsoft reveal the threat actor probably worked together with DEV-1084 to pull off the attack, the latter of which conducted the destructive actions after MuddyWater successfully gained a foothold onto the target environment.
“Mercury likely exploited known vulnerabilities in unpatched applications for initial access before handing off access to DEV-1084 to perform extensive reconnaissance and discovery, establish persistence, and move laterally throughout the network, oftentimes waiting weeks and sometimes months before progressing to the next stage,” Microsoft said.
In the activity detected by Redmond, DEV-1084 subsequently abused highly privileged compromised credentials to perform encryption of on-premise devices and large-scale deletion of cloud resources, including server farms, virtual machines, storage accounts, and virtual networks.
Furthermore, the threat actors gained full access…