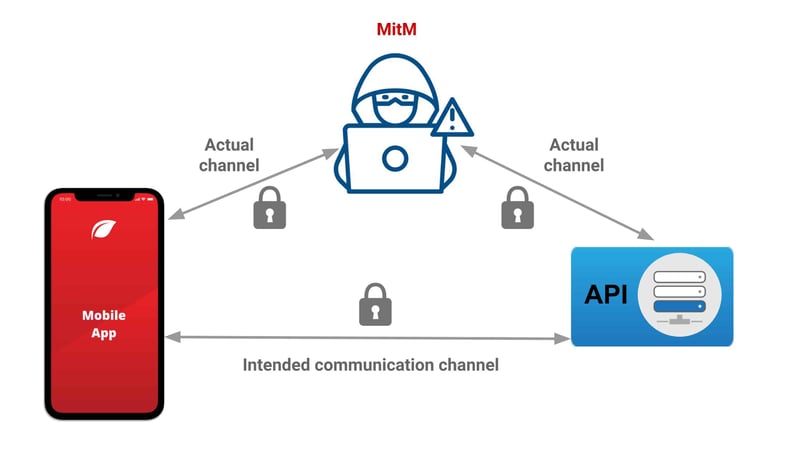
Graduate Certificate Computer Security and Privacy
Who is Computer Security and Privacy Certificate program for?
Drexel College of Computing & Informatics’ Post-Baccalaureate/Graduate Certificate in Computer Security and Privacy provides broad technical expertise in software security, network security and computer privacy. It includes introductory courses in security engineering and computer privacy that cover the technical fundamentals. Electives provide additional in-depth expertise in operating systems, computer networks and cryptography which are essential bodies of knowledge to be able to do technical work in modern computer security. This program is designed to prepare working professionals to meet this demand by providing deep technical expertise in computer security and privacy.
This certificate can be combined with other certificates and/or courses to create the Master of Science degrees listed below.
Fast Facts
Curriculum
IMPORTANT NOTE: Drexel operates on the quarter, not semester, system, offering classes during four 10-week terms throughout the year.
Please visit Drexel’s Course Catalog for a full description of each required and elective course for this program. You can also find a sample Plan of Study for the certificate.
Admissions Requirements
- A completed application for the online format or on-campus format.
- A four-year bachelor’s degree or Master’s degree from a regionally accredited institution in Computer Science, Software Engineering or related STEM degree plus work experience equal to Drexel’s Post-Baccalaureate Certificate in Computer Science Foundations.
- A GPA of 3.0 or higher, in a completed degree program, bachelor’s degree or above.
- Official final transcripts from ALL Colleges/Universities attended. Please note: For students who have attended an institution outside of the US, it is highly recommended to submit a NACES approved course-by-course transcript evaluation (i.e., WES) for expedited review of your application. This approved evaluation will take the place of the transcript requirement to complete your application.
- Graduate Record Examination (GRE) Scores (must be five years old or less) are not required but recommended for international students and…