How to Hunt for Ransomware with Combined PAN XSOAR Integrations
Here’s how to automate your file analysis routines and protect your valuable data from ransomware cyber criminals.
Through the years, ReversingLabs security solutions have been integrated with numerous third-party ecosystems and platforms, including IBM SOAR, Anomali ThreatStream, Splunk and Microsoft Azure cloud. Each integration is designed and developed to bring valuable ReversingLabs intelligence and data to users of as many cybersecurity platforms as possible.
The same goes for Palo Alto Networks Cortex XSOAR (XSOAR) — a well known and respected SOAR (Security Orchestration, Automation and Response) platform. There is a bundle of well crafted threat analysis apps developed by ReversingLabs and available on the XSOAR Marketplace. SOAR platforms enable threat analysts to create their own workflows and reactions to various security-related situations and incidents using data enrichment apps, data feeds and action playbooks.
Here’s how each of the mentioned types of tools ReversingLabs offers can be used with XSOAR.
Indicator Feed App: The Source of Ransomware Intelligence
If you want to perform detailed analysis on a large indicator dataset using a SOAR platform, first you need to bring the data to the platform. ReversingLabs’ Ransomware and Related Tools Feed for XSOAR brings in data that is already analyzed, labeled and assigned a certain malware reputation. Each indicator itself in this data feed is related to an instance of ransomware found in the wild, or in any possible way connected to ransomware activity. Each indicator is connected either to an ongoing, or a very recent, ransomware campaign. This is where the value of such a feed lies: The data is derived from numerous sources providing fresh and relevant malware information.
The Ransomware and Related Tools Feed
ReversingLabs Ransomware and Related Tools Feed for XSOAR currently provides four types of indicators:
- file hashes
- IPv4 addresses
- URLs
- domains
Each of these indicator types carries a lot of common types of metadata with additional information specific to each.
After installing and configuring the feed app, the indicators start flowing into XSOAR’s Threat Intel.
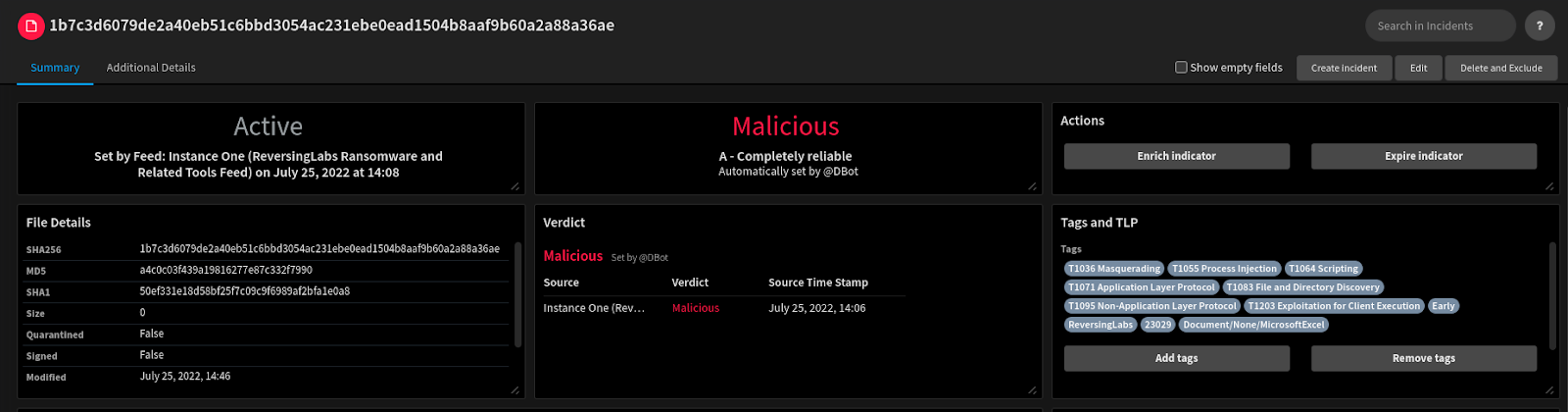 Figure 1: File hash indicator…
Figure 1: File hash indicator…