Androxgh0st Malware Compromises Servers Worldwide for Botnet Attack
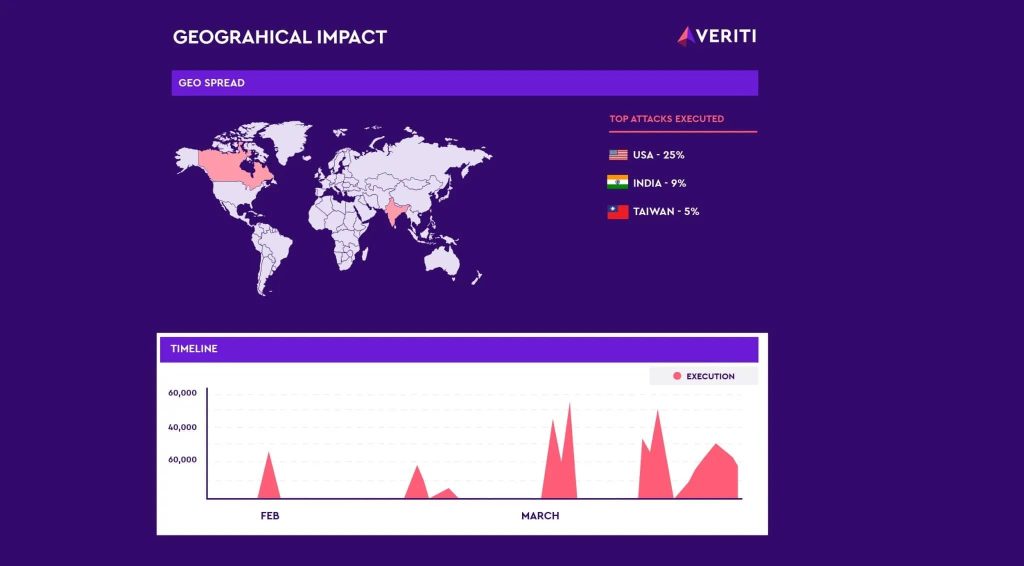
Veriti Research has discovered a surge in attacks from operators of the Androxgh0st malware family, uncovering over 600 servers compromised primarily in the U.S., India and Taiwan.
According to Veriti’s blog post, the adversary behind Androxgh0st had their C2 server exposed, which could allow for a counterstrike by revealing the impacted targets. The researchers then went on to alert the victims.
Further research revealed that Androxgh0st operators are exploiting multiple CVEs, including CVE-2021-3129 and CVE-2024-1709 to deploy a web shell on vulnerable servers, granting remote control capabilities. Moreover, evidence suggests active web shells associated with CVE-2019-2725.
Androxgh0st Threat Actor Ramps Up Activity
Hackread.com has been tracking Androxgh0st operations since was first noticed in December 2022. The malware operator is known for deploying Adhublika ransomware and was previously observed communicating with an IP address associated with the Adhublika group.
Androxgh0st operators prefer exploiting Laravel applications to steal credentials for cloud-based services like AWS, SendGrid, and Twilio. They exploit vulnerabilities in Apache web servers and PHP frameworks, deploying webshells for persistence.
However. their recent focus seems to be building botnets to exploit more systems. Recently, the FBI and CISA issued a joint Cybersecurity Advisory (CSA) advisory, warning about Androxgh0st constructing a botnet to carry out credential theft and establish backdoor access.
Last year, Cado Security Ltd. revealed the details of a Python-based credential harvester and a hacking tool called Legion, linked to the AndroxGh0st malware family. Legion is designed to exploit email services for abuse.
The Way Forward
Veriti’s research goes onto show the importance of proactive exposure management and threat intelligence in cyber security. Organizations must regularly update their security measures, including patch management for known vulnerabilities, strong web shell deployment monitoring, and behavioural analysis tools to prevent breaches and protect against similar vulnerabilities.