Jaw-Dropping New Hack Turns Your Phone Screen Into Covert Spy Camera
Hackers could use smartphone ambient light sensors to spy on users, MIT researchers say
In a new study published in Science Advances, researchers from the Massachusetts Institute of Technology Computer Science and Artificial Intelligence Laboratory have revealed how hackers can turn your smartphone into a spying device akin to the TV screens featured in Orwell’s 1984.
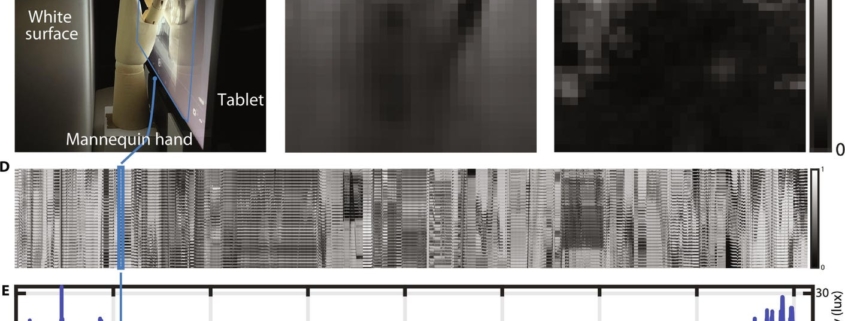
The paper, Imaging privacy threats from an ambient light sensor, reveals how seemingly harmless ambient light sensors, used in most smartphones to auto-adjust screen brightness, are capable of covertly capturing user interactions thanks to a newly developed computational imaging algorithm.
How Smartphone Screens, Not Cameras, Can Spy On Users
I have written plenty of articles covering how seemingly innocuous items can be used to spy on users and create a security threat that one might not ordinarily imagine. Forget the more obvious targets for such stories as smart speakers, and think more about light bulbs and vacuum cleaners, both of which have been subject to research regarding covert surveillance techniques.
More than a hint of 1984 shines through the research by Yang Liu, Gregory W. Wornell, William T. Freeman and Fredo Durand. Instead of Big Brother keeping tabs on citizens through enormous TV screens everywhere, the researchers talk of how hackers could covertly capture user gestures through the small screens we carry everywhere: smartphones.
More precisely, the researchers focus on the ambient light sensors that enable our smartphones to adjust screen brightness to match our environment. Apps can use ambient light sensors without the need to ask permission from the user. The lack of permission control is not exactly surprising, given that such sensors have not been considered a privacy or security risk. Until now.
Novel Smartphone Security Risk Revealed By MIT Researchers
“The ambient light sensor needs to be always on for functionality and is…