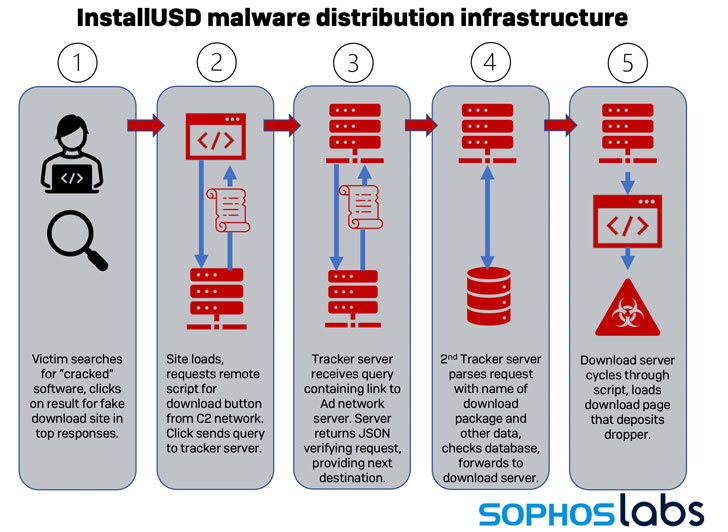
Qakbot Cracked: FBI and Friends Hack the Hackers
 Operation Duck Hunt shoots to kill big botnet.
Operation Duck Hunt shoots to kill big botnet.
Qakbot is dead. The world’s biggest “loader” botnet has ceased to be. It’s a stiff. Bereft of life, it rests in peace—thanks to the U.S. Justice Department and European partners.
Also known as Qbot, Oakboat and Pinkslipbot, Qakbot has rung down the curtain. In today’s SB Blogwatch, we’ve gone to join the choir invisible.
Your humble blogwatcher curated these bloggy bits for your entertainment. Not to mention: Blue Skies.
Or is it just resting? Beautiful plumage.
What’s the craic? Christopher Bing and David Ljunggren report—“Partners have taken down notorious ‘Qakbot’ hacking network”:
“Originates from Russia”
An international law enforcement operation [has] taken down the notorious “Qakbot” malware platform used … in a variety of financial crimes. … The operation, nicknamed Duck Hunt, [also] involved … France, Germany, the Netherlands, Britain, Romania and Latvia.
…
U.S. attorney Martin Estrada said the move against Qakbot was the most significant technological and financial operation ever led by the [DoJ] against a botnet [and] as part of the operation, agencies seized 52 servers. [Qakbot] had infected more than 700,000 victim computers … and caused hundreds of millions of dollars in damage.
…
First discovered more than a decade ago, Qakbot is commonly spread through malicious, boobytrapped email. … Security researchers say they believe Qakbot originates from Russia.
How? Lawrence Abrams explains—“How the FBI nuked Qakbot malware from infected Windows PCs”:
“Authorized by a judge”
Qakbot, aka Qbot and Pinkslipbot, started as a banking Trojan in 2008. … However, over time, the malware evolved into a malware delivery service utilized by other threat actors. … In the past, Qakbot has partnered with multiple ransomware operations, including Conti, ProLock, Egregor, REvil, RansomExx, MegaCortex … Black Basta and BlackCat/ALPHV.
…
The FBI [was] able to dismantle the botnet by seizing the attacker’s server infrastructure and creating a special removal tool that uninstalled the Qakbot malware. … They accessed the encryption keys [and] used an infected device under…