FCC is Looking to Update its Definition of Broadband – Broadband Breakfast
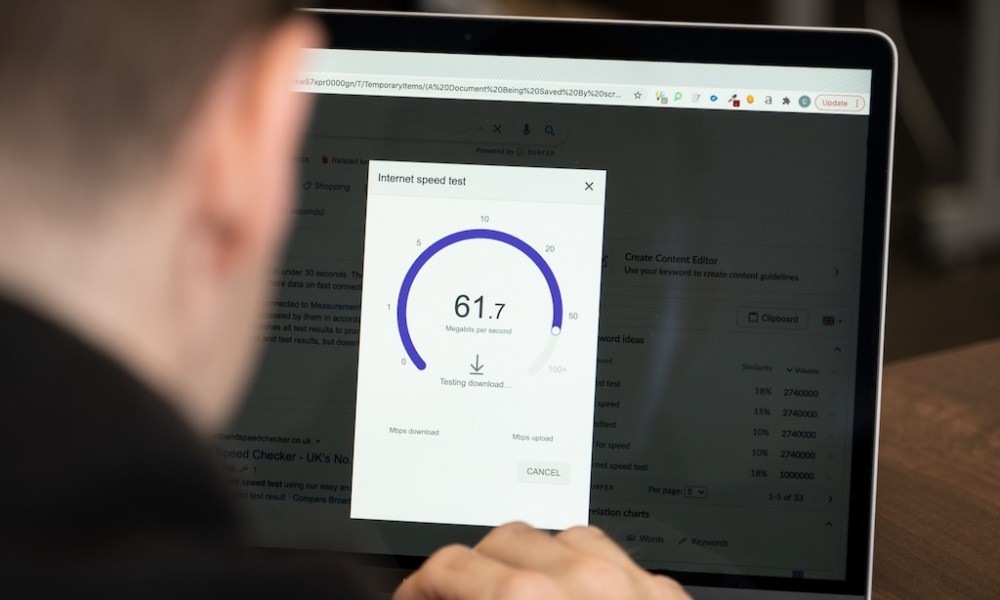
WASHINGTON, September 26, 2023 – Industry associations are praising a proposal from the Federal Communications Commission Thursday to review coverage areas based on updated commission maps so that the 5G Fund can reach more communities without the wireless technology.
Thursday’s vote proposes to help dictate the eligibility requirements for areas in need of support of the 5G Rural Fund for America.
The commission proposed adjusting the $9-billion budget allocated for the 5G Fund, the optimal methodology for consolidating eligible areas into smaller geographic regions for bidding, the feasibility to extend 5G Fund support to qualifying regions in Puerto Rico and the U.S. Virgin Islands, possibly mandating cybersecurity and supply chain risk management plans for 5G Fund recipients, and the possibility of whether the 5G Fund should be utilized to encourage the deployment of Open Radio Access Networks.
“What this means is that as we develop the 5G Fund and build the successor to our existing universal service program supporting wireless networks in rural America, known as the Mobility Fund, we will be able to incorporate this detailed picture of where service is and is not,” FCC Chairwoman Jessica Rosenworcel said. “We will be able to see gaps in coverage and ensure support actually reaches the communities that need it most.”
Meredith Attwell Baker, president and CEO of industry association CTIA, praised the commission’s decision “for recognizing the crucial role that mobile wireless services play in keeping Americans connected.”
“Implementing the 5G Fund and using the FCC’s new maps will help extend the benefits of advanced 5G services to more communities and consumers,” she said.
Tim Donovan, president and CEO of the Competitive Carriers Association, also praised the decision, saying the 5G Fund “has been a top priority for CCA, and we will continue to work with the Commission and our members to ensure the final rules preserve and expand mobile broadband access to every American.”
The commission also adopted Thursday new regulations to expedite space applications, the availability of spectrum resources for space launches, old rules to…