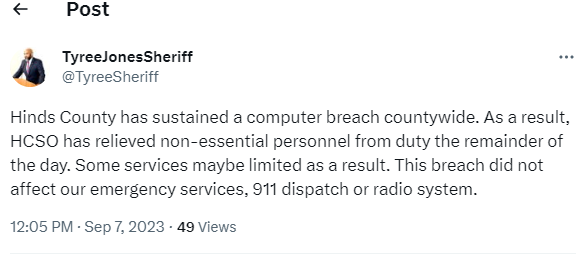
Computer system breach ends work day early
A computer system breach shut down operations for Hinds County employees Thursday. Hinds County Tax Collector Eddie Fair confirmed that internal servers were hacked and access to computers was not granted. Employees were sent home for the day while an investigation into what caused the service interruption is conducted. Residents in Hinds County will not be able to purchase car tags or receive any services. Hinds County Sheriff Tyree Jones said the breach did not affect our emergency services, 911 dispatch or the radio system. This is developing. Stay with WAPT for updates on when offices could reopen.
A computer system breach shut down operations for Hinds County employees Thursday.
Hinds County Tax Collector Eddie Fair confirmed that internal servers were hacked and access to computers was not granted. Employees were sent home for the day while an investigation into what caused the service interruption is conducted.
Residents in Hinds County will not be able to purchase car tags or receive any services.
Hinds County Sheriff Tyree Jones said the breach did not affect our emergency services, 911 dispatch or the radio system.
This is developing. Stay with WAPT for updates on when offices could reopen.