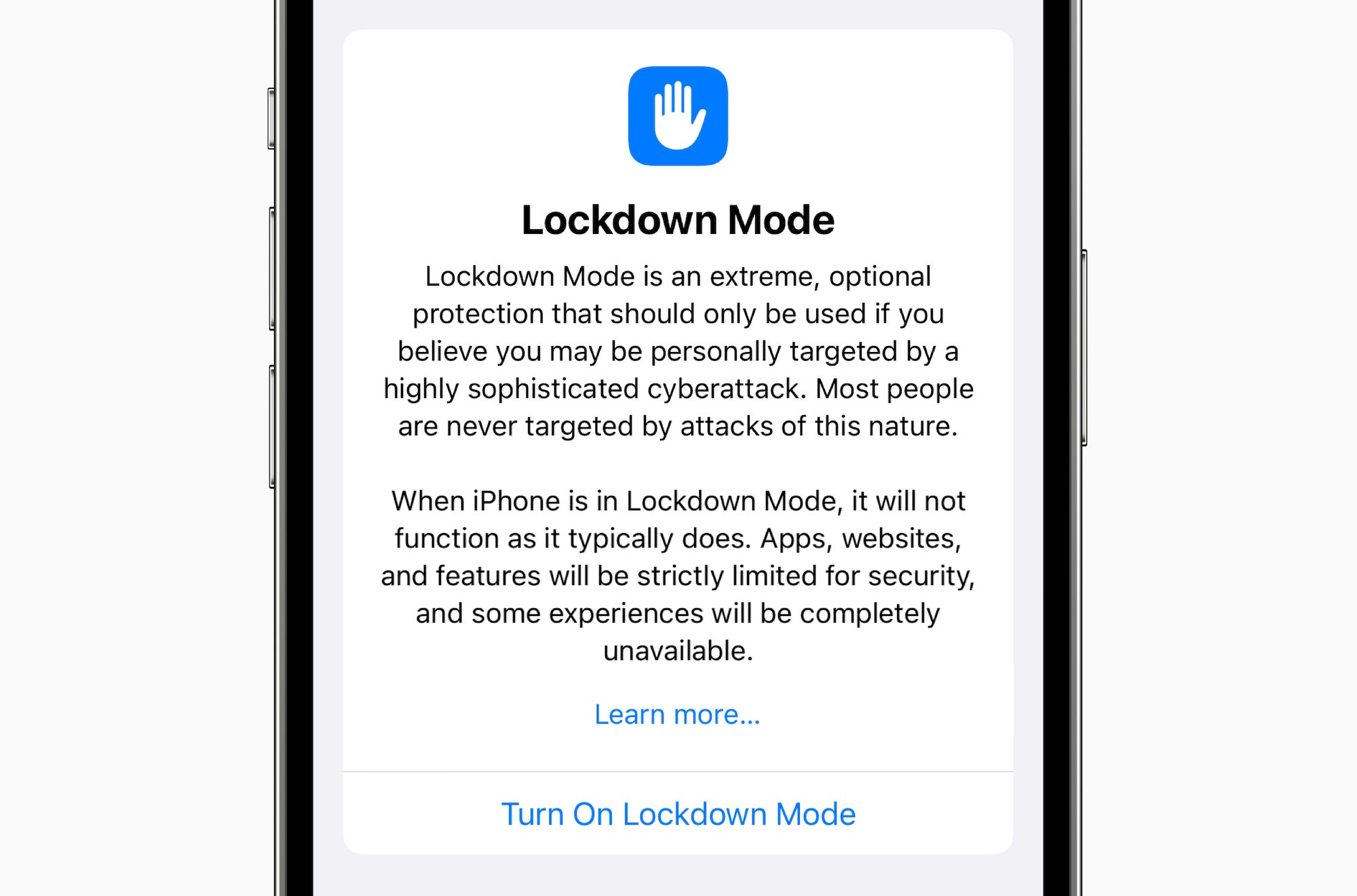
This week, Apple announced a new “extreme, optional” security feature called Lockdown Mode that is aimed at a very small minority of users who are at risk of being deliberately targeted by cyberattacks “from private companies developing state-sponsored mercenary spyware.” It will launch with iOS 16, iPadOS 16, and macOS Ventura this fall.
Lockdown Mode is designed to block a category of hyper-targeted hacks that are generally used by governments (or private companies with support from governments) against activists, dissidents, journalists, and high-level business people. Although there are presumably other, similar exploits that have not been exposed, the most infamous of these is the spyware called Pegasus.
Pegasus, developed by the (now sanctioned) Israeli technology firm NSO Group, turns iPhones and Android smartphones against their users. It’s basically the stereotypical Hollywood hack: The attackers have access to pretty much everything on the device, can intercept calls and messages, and even use the microphone, camera, and GPS to record and track people. Crucially, Pegasus can be a “zero-click” exploit, meaning that it can be installed without the user doing anything; at one point, phones could even be infected through a missed WhatsApp voice call.
Cybersecurity typically involves a tradeoff between convenience and security. If you want your computer to be very difficult to hack, don’t connect it to the internet—lock it in a secure room in your house. No viruses! But also no email, Amazon, or Minecraft. Modern iPhones, iPads, and Macs come with loads of features that make them fast, convenient, and easy to use, but these same features also give hackers large “attack surfaces” to work with. Lockdown Mode turns off a lot of these features, or at least makes them disabled by default, at the expense of a great user experience.
Some of the features that get disabled by Lockdown Mode, for example, are the speed and efficiency technologies in a bit of software called WebKit (which powers Safari). Web pages that haven’t been flagged as “trusted” will take longer to load and may be jankier to use, but those web pages…