MrB Ransomware (.mrB Files) – Analysis & File Decryption – Gridinsoft Blog
MrB ransomware is a new Dharma ransomware sample, discovered on February 21, 2024. It is distinctive for applying a complex extension to the encrypted files that ends up with “.mrB”. This ransomware primarily attacks small corporations and asks the ransom only for decrypting the files, i.e. it does not practice double extortion. Jakub Kroustek was the first to discover and report this ransomware sample.
What is mrB Ransomware?
As I’ve described in the introduction, mrB is a sample of Dharma ransomware, a malware family active since 2016. It is known for adding a long extension to every file it encrypts; it consists of the victim ID, contact email and the extension itself. At the end, the encrypted file name starts looking like this:
Media1.mp3 → Media1.mp3.id-C3B22A85.[mirror-broken@tuta[.]io].mrB
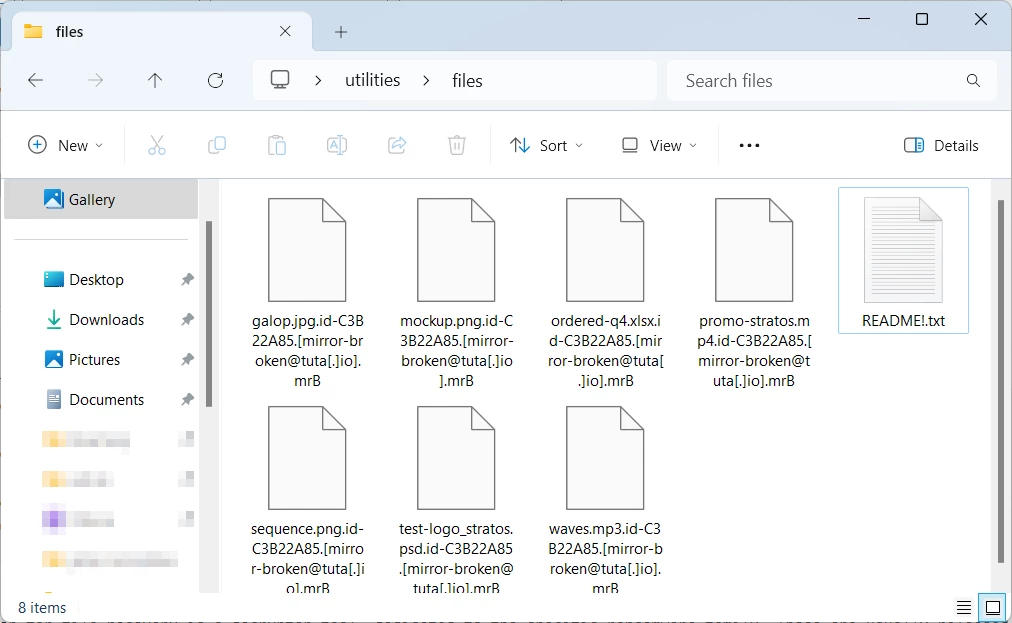
MrB ransomware encrypts a wide range of file formats, from images and documents to files of some specific software suites. After finishing the encryption, it opens a pop-up ransom note in a form of HTA file, and also spawns a readme text file. The latter appears in every folder that contains the encrypted files. Below, you can see the contents of both ransom notes.
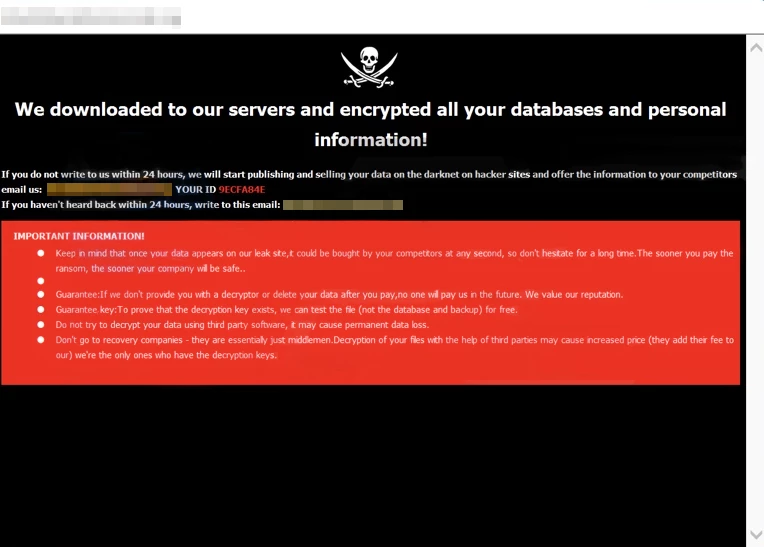
Contents of the readme text file:
Your data has been stolen and encrypted! email us mirror-broken@tuta[.]io
How to Recover Encrypted Files?
Unfortunately, there are no recovery options available for mrB ransomware. The imperfections in its early Dharma samples were used to make the decryptor, though the flaws were fixed, and it is not effective nowadays. Options you can find online, like “professional hackers” or file recovery services will at best act as a medium between you and the hackers. At worst, they will take your money and disappear.
The most effective option for file recovery is a decryptor tool, dedicated to the specific ransomware family. Those are usually released when a vulnerability in the encryption mechanism is found, or when ransomware servers are seized. It may sound like it is unlikely to happen, but there were 4 such decryptors released in the first months of 2024. Be patient, do not lose hope – and you get the files back.
For now, your best…