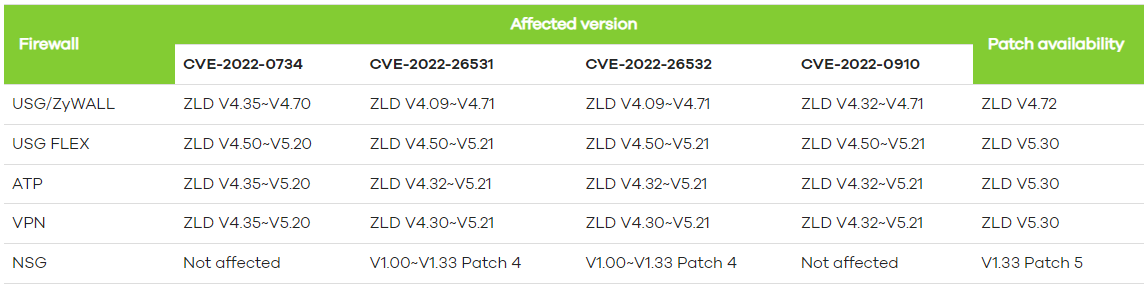
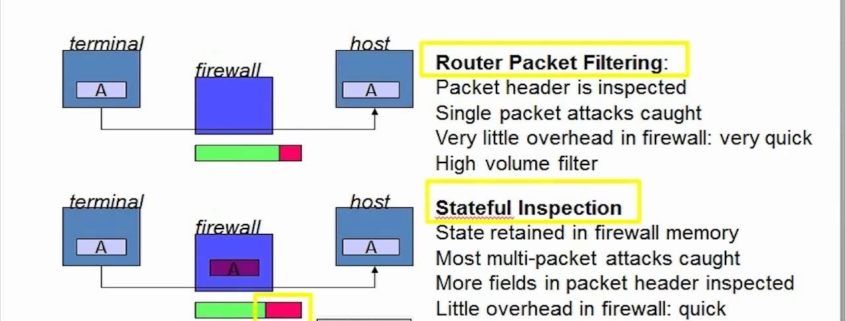
Cisco’s Talos security intelligence group issued a warning today about an uptick in highly sophisticated attacks on network infrastructure including routers and firewalls.
The Cisco warning piggybacks a similar joint warning issued today from The UK National Cyber Security Centre (NCSC), the US National Security Agency (NSA), US Cybersecurity and Infrastructure Security Agency (CISA) and US Federal Bureau of Investigation (FBI) that noted an uptick in threats in part utilizing an exploit that first came to light in 2017. That exploit targeted an SNMP vulnerability in Cisco routers that the vendor patched in 2017.
But as Cisco and the government agencies noted, similar exploits are being aimed at a broad set of multivendor networking gear, potentially including Juniper, Extreme, Allied-Telesis, HP and others.
“The warning involves not just Cisco equipment, but any networking equipment that sits at the perimeter or that might have access to traffic that a significantly capable and well-tooled adversary might have an interest in intercepting and modifying,” said JJ Cummings, Cisco Talos Threat Intelligence & Interdiction team lead. Cummings leads the Talos team tasked with nation-state, critical infrastructure, law enforcement, and intelligence-based concerns.
In a blog noting the increase in threats, Cisco Talos wrote: “We have observed traffic manipulation, traffic copying, hidden configurations, router malware, infrastructure reconnaissance, and active weakening of defenses by adversaries operating on networking equipment. Given the variety of activities we have seen adversaries engage in, they have shown a very high level of comfort and expertise working within the confines of compromised networking equipment.”
National intelligence agencies and state-sponsored actors across the globe have attacked network infrastructure as a primary target, Cisco stated. “Route/switch devices are stable, infrequently examined from a security perspective, are often poorly patched and provide deep network visibility.”
“The idea here is to get the messaging out that network operations teams need to maybe start to approach things slightly differently or…