Allies To Gain Access to US Ransomware Data Under New Policy

The White House is set to announce a new policy for responding to ransomware attacks, as the number of such attacks continues to grow substantially. The US accounts for 46% of ransomware attacks globally, according to Anne Neuberger, Deputy National Security Advisor.
Recent high-profile attacks have hit major companies like casino operator MGM Resorts and cleaning products maker Clorox. In these attacks, hackers encrypt systems and demand ransom payments, usually in cryptocurrency, to decrypt them. Sensitive stolen data is often used to further extort victims.
The new White House policy will facilitate intelligence sharing related to ransomware attackers between the US and its allies. In particular, authorities will share cryptocurrency wallet addresses criminals use to collect ransoms.
The policy reflects the increasingly interconnected nature of ransomware schemes. Attackers routinely use infrastructure and data from one country to attack organizations in others. Enhanced coordination will allow rapid response.
A 40-country alliance led by the US, including Nigeria, Singapore and South Korea, will collaborate to cut off ransomware funding flows. The group will leverage artificial intelligence to trace ransom payments on the blockchain and maintain a blacklist of known criminal wallets.
“Ransomware attackers extorted at least $456.8 million from victims in 2022, down from $765.6 million the year before,” Chainalysis reported.
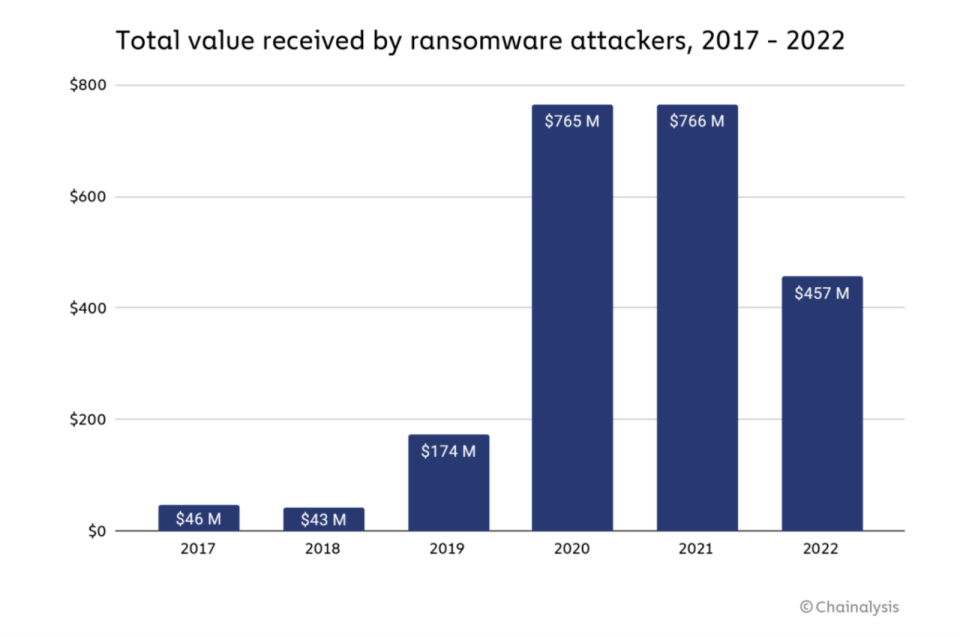

Source: Chainalysis
With this alliance, authorities hope to stem the tide of attacks. But with billions in cryptocurrency paid annually to ransomware criminals, curbing the epidemic remains an ongoing battle.




