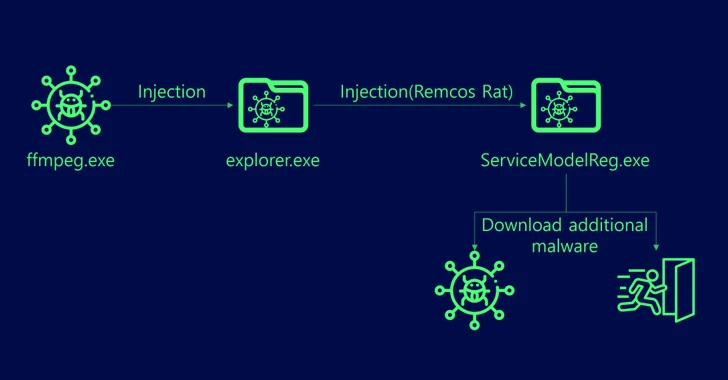
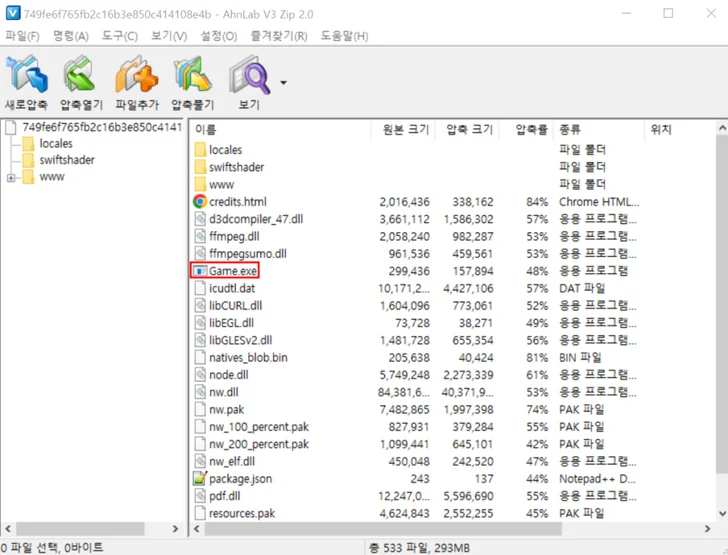
Bitcoin-Stealing Malware Disguised as Cheat Software for Popular Games; Millions of Gamers at Risk
Many gamers looking for third-party cheat software to gain a competitive edge in popular titles like Call of Duty (COD), Diablo, and World of Warcraft (WoW) have had their Electrum Bitcoin wallets drained by malware.
This malware campaign, orchestrated by an unidentified actor, potentially affected over 4.9 million gaming accounts across various platforms, info security firm VX Underground said on Wednesday. The exact amount of funds stolen from users is unknown at this time.
On Thursday, TechCrunch said the malware was first uncovered by COD cheat software developer “Zeebler,” who warned gamers about the threat.
“The scope of the impact is so large, and in a bizarre twist of fate, Activision Blizzard is coordinating with cheat providers to aid users impacted by the massive infostealer campaign,” VX Underground said on X (formerly Twitter).
About 4.9 Million Gaming Accounts at Risk
According to VX Underground, the crypto-swiping malware may have impacted 561,183 Activision accounts, 3,662,627 million Battle.net accounts, 117,366 ElitePVPers accounts, 572,831 UnknownCheats accounts, and 1,365 PhantomOverlay accounts.
“When Elite PVPers was approached by PhantomOverlay administrative staff about the compromised accounts, Elite PVPers confirmed they have identified 40,000+ valid user accounts compromised,” VX Underground said. “These are seemingly freshly stolen credentials and are not present from previous publicly available credential dumps.”
VX Underground noted that not all victims of the malware attack were seeking cheat software for games. Some were using “software for latency improvement (?), VPNs, and Controller Boosting software.”
A source told TechCrunch that Activision Blizzard is trying to “help remove the malware” and is “working on identifying and remediating player accounts for anyone affected.” Meanwhile, Activision spokesperson Delany Simmons told the news outlet that the company’s servers “remain secure and uncompromised.”
It isn’t uncommon for hackers to target gamers with compromised software. In June 2023, Cyble Research & Intelligence Labs said threat actors are using trojanized versions…