Unveiling the Hidden Dangers of the Internet: Why Internet Security Matters
In today’s digital age, the Internet has become an integral part of our lives. It offers unparalleled convenience, endless information, and countless opportunities for connecting with others around the world. However, amidst this vast virtual landscape lies a hidden danger that can wreak havoc on our personal lives and even threaten national security: internet security breaches. In this blog post, we will explore the lurking dangers of the online world and shed light on why internet security matters more than ever before. Join us as we unravel the mysteries behind cyber threats and unveil essential tips to keep yourself safe in this interconnected realm. Don’t let your guard down – it’s time to navigate the web with caution.
What is Internet Security?
Internet security is a topic of great importance to individuals and businesses alike. The Internet is an essential part of our daily lives, and any attempt by someone to gain unauthorized access to your personal or business information can be harmful.
There are many different types of threats that could arise while using the Internet, from malware and spyware infections, to data theft and cybercrime. You need to be aware of these risks in order to keep yourself safe online.
Some measures you can take to protect yourself include installing a reliable anti-virus software program, adopting strong passwords, and keeping up-to-date on the latest security patches. There are also other things you can do, such as staying informed about new threats and how best to protect yourself against them, that are outside the scope of this article.
Whether you’re just starting out online or have been happily surfing the web for years without incident, it’s always important to take precautions against potential dangers.
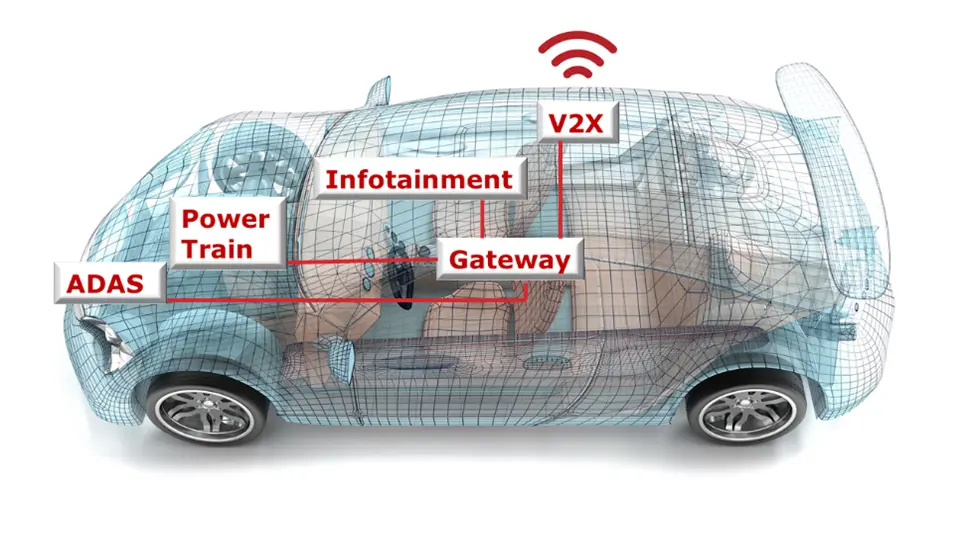
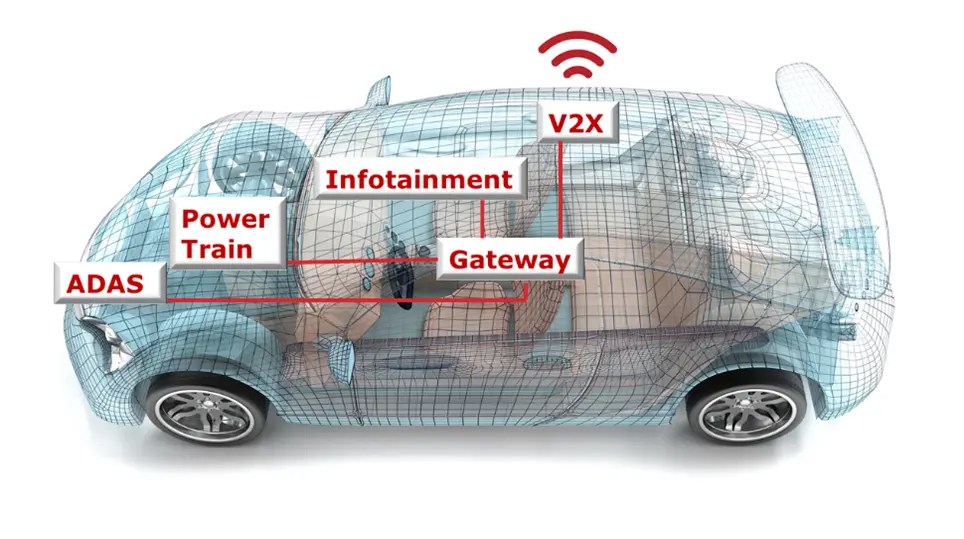
Types of Attacks
There are a myriad of ways that the internet can be used for malicious purposes. Cyber criminals, spies, and trolls use the online world to attack, steal, and manipulate…