Ransomware Payments Exceed $1 Billion in 2023, Hitting Record High After 2022 Decline
Chainalysis got everyone’s attention with their new report. They write, in part:
2023 marks a major comeback for ransomware, with record-breaking payments and a substantial increase in the scope and complexity of attacks — a significant reversal from the decline observed in 2022, which we forewarned in our Mid-Year Crime Update.
Ransomware payments in 2023 surpassed the $1 billion mark, the highest number ever observed. Although 2022 saw a decline in ransomware payment volume, the overall trend line from 2019 to 2023 indicates that ransomware is an escalating problem. Keep in mind that this number does not capture the economic impact of productivity loss and repair costs associated with attacks. This is evident in cases like the ALPHV-BlackCat and Scattered Spider’s bold targeting of MGM resorts. While MGM did not pay the ransom, it estimates damages cost the business over $100 million.
The following figure from their report captures 2023 in terms of the number of different groups, the median ransom payment and frequency of payments per group. A text description is provided in their report.
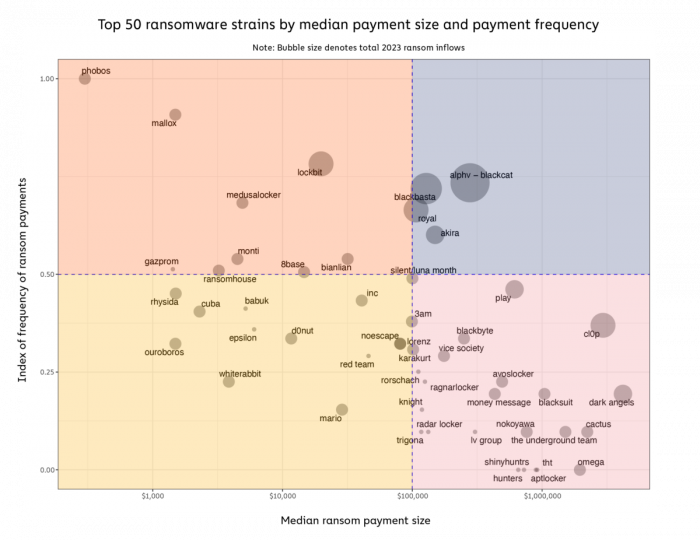
Read more at Chainalysis.