Hacking hotels, Google’s AI goof, and cyberflashing • Graham Cluley

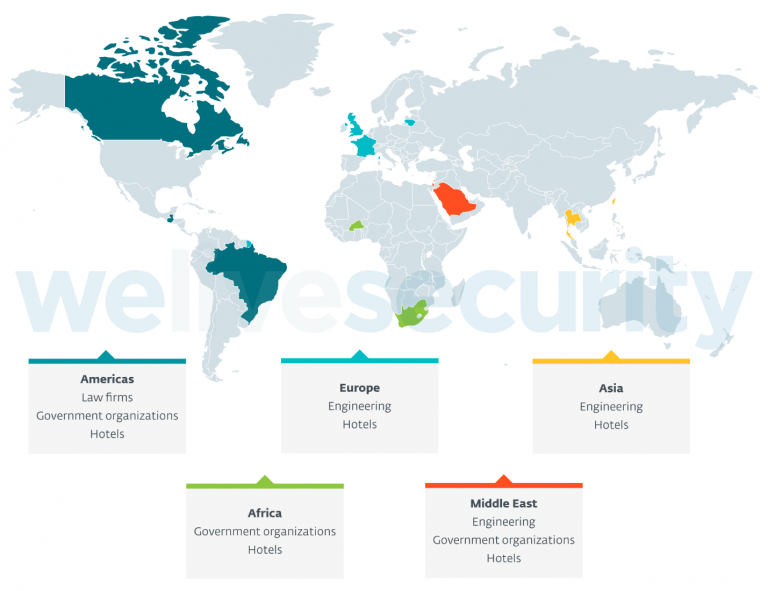
Security researchers find a way to unlock millions of hotel rooms, the UK introduces cyberflashing laws, and Google’s AI search pushes malware and scams.
All this and much much more is discussed in the latest edition of the “Smashing Security” podcast by cybersecurity veterans Graham Cluley and Carole Theriault, joined this week by T-Minus’s Maria Varmazis.
Warning: This podcast may contain nuts, adult themes, and rude language.
Hosts:
Graham Cluley – @gcluley
Carole Theriault – @caroletheriault
Guest:
Maria Varmazis – mstdn.social/@varmazis
Episode links:
Sponsored by:
- Kiteworks – Step into the future of secure managed file transfer with Kiteworks.
- Vanta – Expand the scope of your security program with market-leading compliance automation… while saving time and money. Smashing Security listeners get 20% off!
- Kolide – Kolide ensures that if your device isn’t secure it can’t access your cloud apps. It’s Device Trust for Okta. Watch the demo today!
Support the show:
You can help the podcast by telling your friends and colleagues about “Smashing Security”, and leaving us a review on Apple Podcasts or Podchaser.
Become a supporter via Patreon or Apple Podcasts for ad-free episodes and our early-release feed!
Follow us:
Follow the show on Twitter at @SmashinSecurity, or on Mastodon, on the Smashing Security subreddit, or visit our website for more episodes.
Thanks:
Theme tune: “Vinyl Memories” by Mikael Manvelyan.
Assorted sound effects: AudioBlocks.