Ransomware’s Impact May Include Heart Attacks, Strokes & PTSD
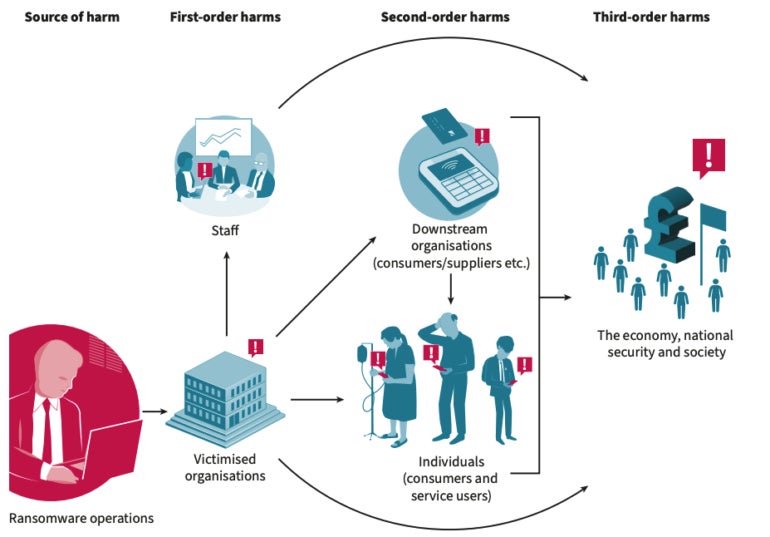
Ransomware incidents cause significant harm at many levels, including to physical and mental health; new research from U.K. security think tank Royal United Services Institute has classified this impact into three categories (Figure A):
- First-order harms: The harms to organizations and their staff. Examples include data loss, reputational harm and heart attacks.
- Second-order harms: The indirect harms to organizations and individuals. Examples include clients and customers in supply chains might be targeted, and patients’ cancer treatments are disrupted.
- Third-order harms: The harms to the wider society, economy and national security. An example includes citizens losing trust in a state’s ability to provide basic services.
Figure A
The RUSI’s research is based on interviews with victims and incident responders of ransomware attacks and reflects “new and existing types of harm to the U.K. and other countries.”
First-order harms: Direct targets of ransomware attacks
The direct targets are organizations and staff directly exposed to ransomware.
Infrastructure harm
Organizations hit by a ransomware attack may suffer physical or digital harm to data and systems. Data loss from the encryption of data by ransomware can be devastating, especially if the threat actor manages to also access the backup systems and render them useless. Thousands of computers can also become unusable for their users, forcing organizations to suddenly return to operating “by pen and paper.”
Operational Technology might also be impacted. The increasing convergence of IT and OT leave physical infrastructures more vulnerable to ransomware, even though most ransomware operators lack the capability to directly compromise OT or Industrial Control Systems; one example is when ransomware’s impact on IT prevents other systems (e.g., fire controls, doors, gates or closed circuit television) from working properly.
An organization’s incident response to ransomware might impact business because incident handlers often need to isolate parts of the IT infrastructure to conduct their remediation and recovery operations –…