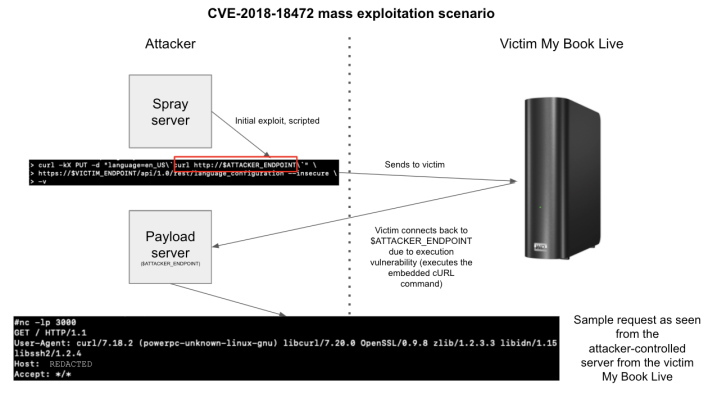
Dutch Police Arrest 3 Hackers Involved in Massive Data Theft and Extortion Scheme
The Dutch police announced the arrest of three individuals in connection with a “large-scale” criminal operation involving data theft, extortion, and money laundering.
The suspects include two 21-year-old men from Zandvoort and Rotterdam and an 18-year-old man without a permanent residence. The arrests were made on January 23, 2023.
It’s estimated that the hackers stole personal data belonging to tens of millions of individuals. This comprised names, addresses, telephone numbers, dates of birth, bank account numbers, credit cards, passwords, license plates, social security numbers, and passport details.
The Politie said its cybercrime team started the investigation nearly two years ago, in March 2021, after a large Dutch company suffered a security breach.
The name of the company was not disclosed but some of the firms that were hit by a cyber attack around that time included RDC, Shell, and Ticketcounter, the last of which was also a victim of an extortion attempt.
“During the course of the investigation, it has become clear that thousands of small and large companies and institutions, both national and international, have fallen victim to computer intrusion (hacking) in recent years, followed by theft and handling of data,” the agency said.
The attack spree targeted a wide range of industry verticals spanning catering, training institutes, e-commerce, software, social media, and critical infrastructure.
Describing it as a “sophisticated” operation, the Politie said the threat actors demanded a Bitcoin payment from the affected companies and threatened to publish the stolen information online or destroy the digital infrastructure, racking up millions in damages.
The ransom demanded per company is said to have ranged anywhere between €100,000 and €700,000. To make matters worse, the suspects ended up selling the data despite the companies paying up.
The sensitive nature of the plundered information means that it could be used to carry out social engineering attacks and various kinds of fraudulent activities.
“Data theft and data trading is a huge revenue model for criminals,” the Politie warned. “Not just by extorting companies. The…