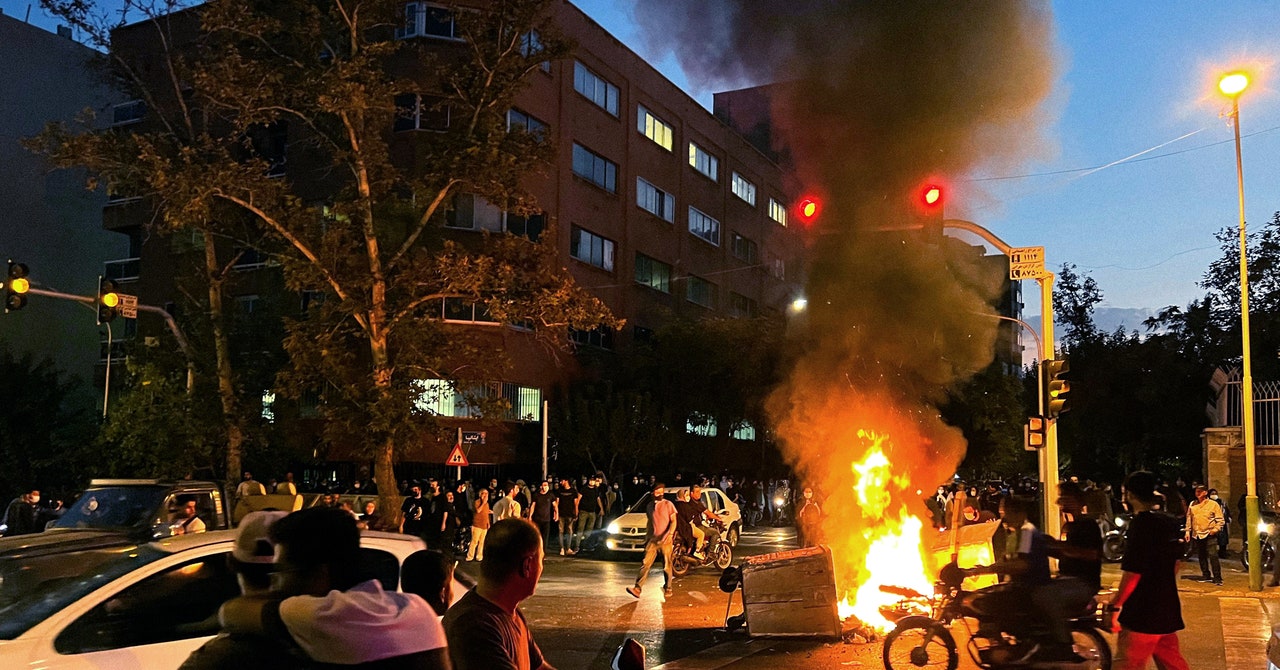Iran’s internet price rises, and so does the fear of greater censorship
Iranians could pay up to 34% more for the internet in 2024 as providers get the green light from the government to increase their tariffs.
Deemed as a move to balance persistent high levels of inflation, many commentators fear that less affordable internet rates could exacerbate ongoing issues with online censorship while discouraging citizens from accessing digital services.
Authorities have long been attempting to control the information users can and cannot access—especially during times of protests. As a result, Iranians have turned en masse to VPN services as a way to bypass restrictions. More expensive internet rates seem to be yet another way to limit people’s online activities.
An expensive restricted internet
“In an environment of political unrest and regular protests, reliable and affordable internet is crucial for maintaining social connections and staying informed, making this new barrier to connect to the internet all the more devastating,” Lina Survila, spokeswoman for VPN provider Surfshark, told me.
Tehran is infamous for heavily restricting the internet—Surfshark counted 55 instances since 2015. However, this trend considerably intensified at the end of 2022 when a wave of protests erupted, following the news that a 22-year-old Iranian woman had died in the custody of Iran’s morality police for allegedly violating strict hijab rules.
It’s very likely this increase in internet tariffs is an attempt to put online access out of reach for many Iranians
Lina Survila, Surfsjark
Authorities began by throttling internet connections and restricted access to Instagram and WhatsApp as a means to silence protesters.
Weekly disruptions to internet connectivity have also been enforced during Friday prayers in the Zahedan region ever since, making Iran by far the biggest perpetrator of internet shutdowns in 2023.
While a virtual private network (VPN) cannot help during periods of total internet shutdown, it’s a very useful tool for accessing restricted social media platforms and other blocked sites. It spoofs users’ IP addresses, while encrypting internet connections for better privacy.
Put simply, VPNs make government imposed restrictions ineffective—and that’s something…