The long-term psychological effects of ransomware attacks
Northwave has conducted scientific research into the psychological effects of a ransomware crisis on both organizations and individuals. The findings reveal the deep marks that a ransomware crisis leaves on all those affected. It also shows how their IT and security teams can turn in disarray long after the crisis itself has passed.
Key findings on psychological effects of ransomware
“The research reveals how the psychological impact of ransomware attacks can persist on people in affected organizations for a very long time,” explains Organizational Psychologist Inge van der Beijl, Director Behaviour & Resilience at Northwave. “It shows that crisis team members may develop serious symptoms far later. Top management and HRM need to take measures against this, in fact right from the very beginning of the crisis. They are the ones bearing responsibility for the well-being of their staff.”
She continues: “We also discovered how teams haven fallen apart some time after the crisis, with members leaving or staying home on sick-leave. The study reveals that effects can linger throughout the organization. All in all the investigation shows that this invisible impact of a cyber crisis is an issue for the general business management, and certainly also for HRM.”
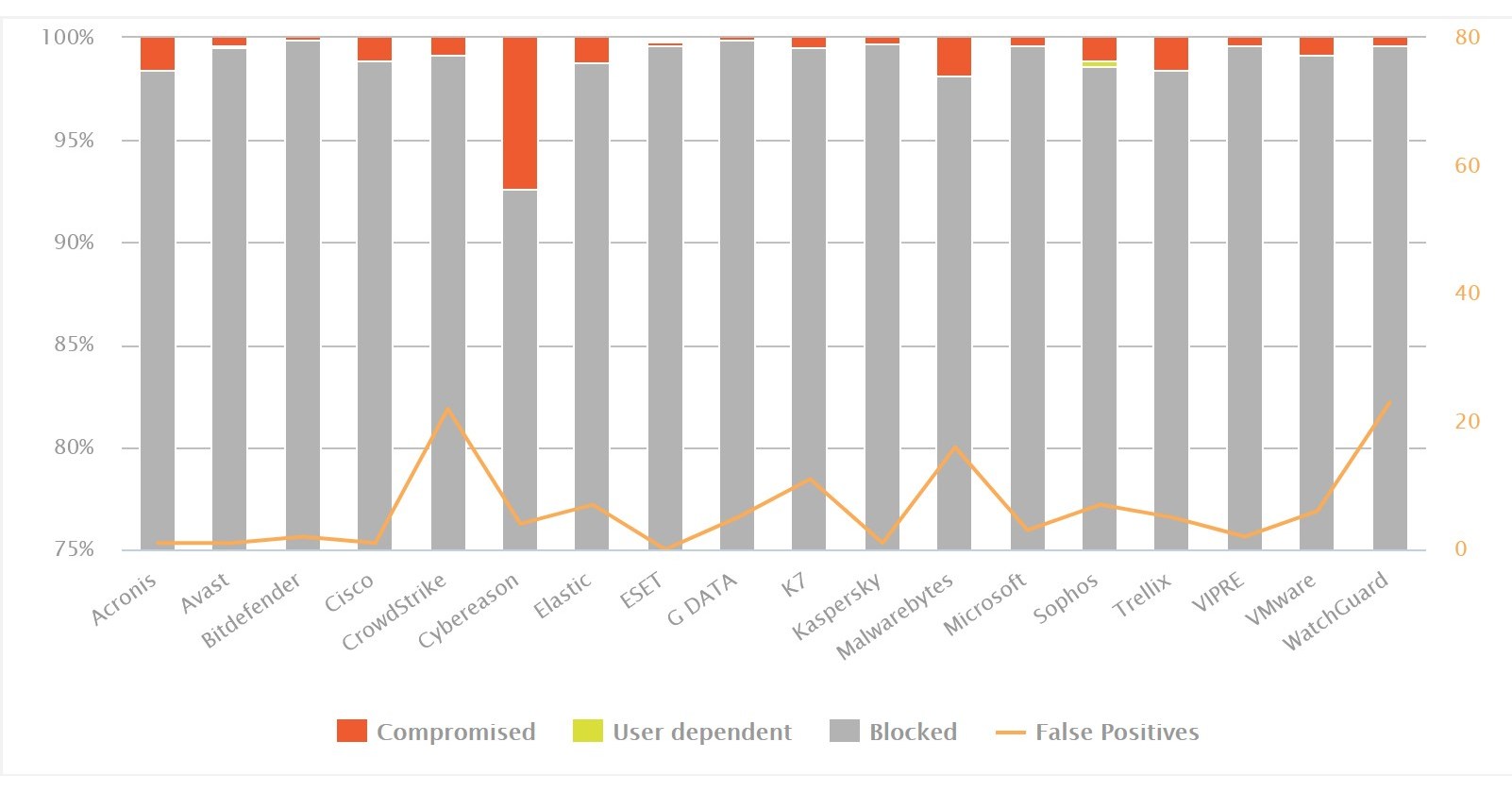
Northwave regards the response to a cyberattack as occurring in three phases. First comes the actual crisis situation, which evolves into an incident phase after about a week. A plan of action is then in place, and recovery measures are launched. The fire has been largely extinguished after a month or so, with the first (basic) functionalities available again.
Full recovery can take one to two years. Each phase has its specific effects on the minds and bodies of those involved, and by extension, on the organization or parts of it. “In average a company is down for three weeks following a malware attack,” notes Van der Beijl. “But it surprised us that the impact persists for so long afterwards. Psychological issues are still surfacing a year after the actual crisis.”
- One of every seven employees involved in the attack, either directly or indirectly, exhibits severe enough symptoms several months later,…