RustDoor macOS Backdoor Targets Cryptocurrency Firms with Fake Job Offers
Several companies operating in the cryptocurrency sector are the target of a newly discovered Apple macOS backdoor codenamed RustDoor.
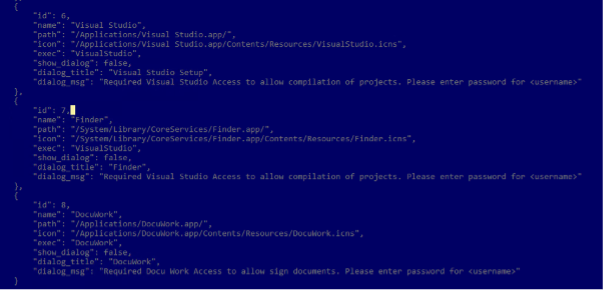
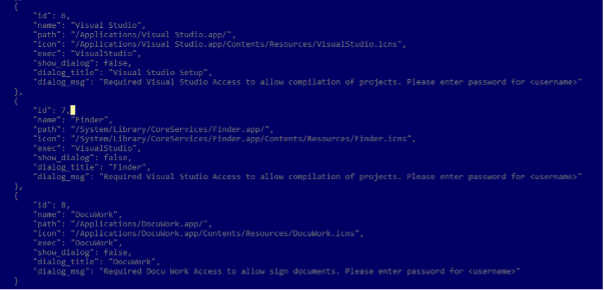
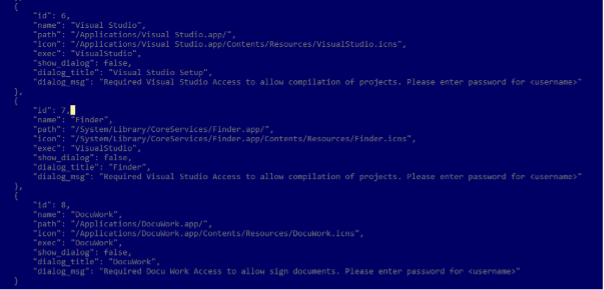
RustDoor was first documented by Bitdefender last week, describing it as a Rust-based malware capable of harvesting and uploading files, as well as gathering information about the infected machines. It’s distributed by masquerading itself as a Visual Studio update.
While prior evidence uncovered at least three different variants of the backdoor, the exact initial propagation mechanism remained unknown.
That said, the Romanian cybersecurity firm subsequently told The Hacker News that the malware was used as part of a targeted attack rather than a shotgun distribution campaign, noting that it found additional artifacts that are responsible for downloading and executing RustDoor.
“Some of these first stage downloaders claim to be PDF files with job offerings, but in reality, are scripts that download and execute the malware while also downloading and opening an innocuous PDF file that bills itself as a confidentiality agreement,” Bogdan Botezatu, director of threat research and reporting at Bitdefender, said.
Since then, three more malicious samples that act as first-stage payloads have come to light, each of them purporting to be a job offering. These ZIP archives predate the earlier RustDoor binaries by nearly a month.
The new component of the attack chain – i.e., the archive files (“Jobinfo.app.zip” or “Jobinfo.zip”) – contains a basic shell script that’s responsible for fetching the implant from a website named turkishfurniture[.]blog. It’s also engineered to preview a harmless decoy PDF file (“job.pdf”) hosted on the same site as a distraction.
Bitdefender said it also detected four new Golang-based binaries that communicate with an actor-controlled domain (“sarkerrentacars[.]com”), whose purpose is to “collect information about the victim’s machine and its network connections using the system_profiler and networksetup utilities, which are part of the macOS operating system.
In addition, the binaries are capable of extracting details about the disk via “diskutil list” as well…