Notorious ransomware provider LockBit taken over by law enforcement
Washington — A ransomware service provider that has targeted over 2,000 systems across the globe, including hospitals in the U.S., with demands for hundreds of millions of dollars was taken down Monday, and Russian nationals were charged as part of an international plot to deploy the malicious software, the Justice Department announced Tuesday.
Known as LockBit, the network of cybercriminals targets critical components of manufacturing, healthcare and logistics across the globe, offering its services to hackers who deploy its malware into vulnerable systems and hold them hostage until a ransom is paid. The attackers have so far extorted more than $120 million from their victims, officials said, and their program has evolved into one of the most notorious and active.
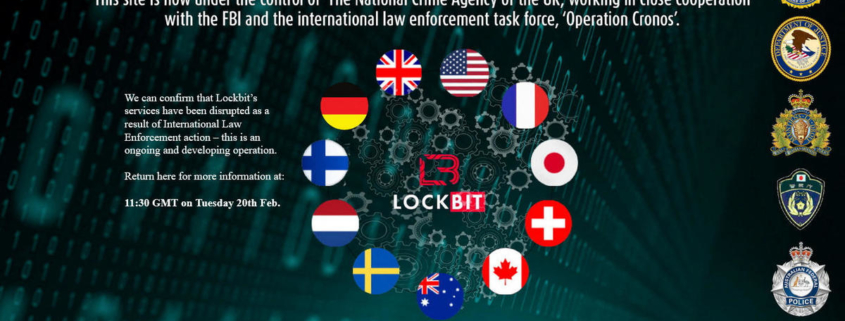
As part of this week’s operation, the FBI and its law enforcement partners in the United Kingdom seized numerous public-facing platforms where cybercriminals could initiate contact with and join LockBit. Investigators also seized two servers in the U.S. that were used to transfer stolen victim data.
The front page of LockBit’s site has been replaced with the words “this site is now under control of law enforcement,” alongside the flags of the U.K., the U.S. and several other nations, the Associated Press noted.
Handout via Reuters
According to Attorney General Merrick Garland, the U.S. and its allies went “a step further” by obtaining the “keys” that can unlock attacked computer systems to help victims “regain access to…