Dangerous permissions detected in top Android health apps
Leading Android health applications expose users to avoidable threats like surveillance and identity theft, due to their risky permissions. Cybernews has the story.
The Android challenge
In the digital age, mobile applications have become an integral part of our lives, transforming the way we communicate, work, and entertain ourselves. With the vast array of apps available at our fingertips, it’s easy to overlook the potential risks they may pose. Behind the sleek interfaces and promising functionalities lurks a hidden concern that has captured the attention of security researchers and users alike – dangerous Android app permissions.
Android, being the most widely used mobile operating system globally, offers developers great flexibility to create innovative and powerful applications. However, this flexibility also introduces a crucial challenge – maintaining a balance between user convenience and safeguarding sensitive data and privacy.
Our researchers took a look at 50 popular health apps – for fitness, sleep tracking, meditation, mental health, quitting smoking, blood-sugar measurement, and medication reminders, among other purposes – to test their permissions.
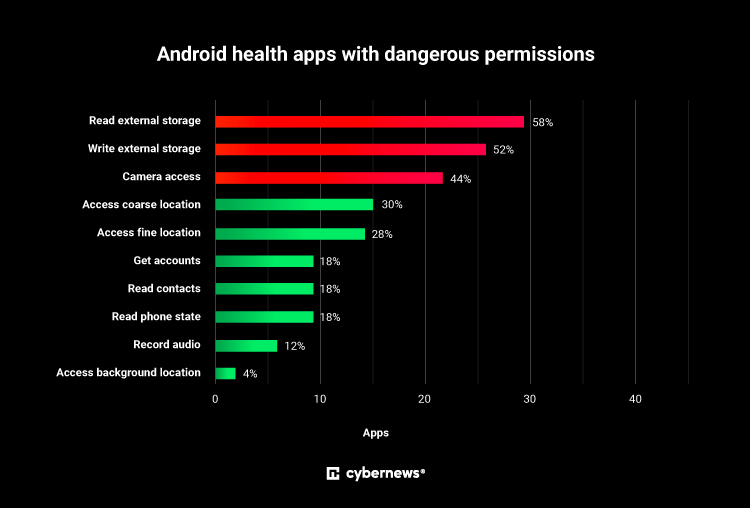
Android permissions
The Android operating system has a comprehensive permission system designed to protect a user’s privacy and security. While many permissions are essential for apps to function properly, some could be considered more dangerous as they grant apps access to sensitive data and functionalities that, if misused, could compromise user privacy and security.
Here are some of the most dangerous Android app permissions:
- Location Access: This permission allows apps to track the user’s precise location using GPS and network information. While some apps genuinely need this permission for features like maps and location-based services, malicious apps could misuse this data for stalking, surveillance, or targeted advertising
- Camera and Microphone Access: Granting an app access to your device’s camera and microphone poses significant privacy risks. Malicious apps with such permissions could spy on users, capture sensitive information, or record audio and video without consent.
- SMS and Call Log Access:…

