Cybercriminals using fewer than 1% of thousands of potential exploits
More than 26,000 vulnerabilities were disclosed in 2023, but cybercriminals only needed fewer than 1% of them, a Qualys Threat Research Unit report reveals. Almost half of exploited vulnerabilities were unknown to cyber defenders.
Statistics from 2023 reveal that malicious actors act fast when exploiting vulnerabilities before they get patched.
Over 26,000 vulnerabilities were disclosed in 2023, which is 5.6% more compared to the previous year. However, Qualys found that fewer than one percent of them contributed to the highest risk and were routinely exploited by threat groups.
Among 206 weaponized vulnerabilities, 109 were known to the US cyber defense agency CISA, while the rest 109 were unknown.
Ransomware groups such as LockBit and Cerber routinely exploited even fewer than that, only 20 vulnerabilities, despite having over 7,000 discovered vulnerabilities with a proof-of-concept exploit code that could result in successful exploitation. Cyber gangs did not use the lower quality code to ensure the highest likelihood of successful attacks.
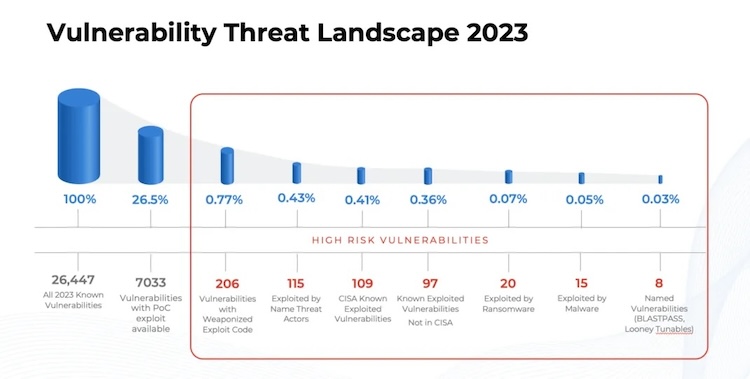
Additionally, 15 vulnerabilities were exploited by malware and botnet groups.
“Many of these vulnerabilities, such as those found in MOVEit Transfer, Windows SmartScreen, and Google Chrome, are exploitable remotely, obviating the need for physical access to the targeted system,” researchers said.
Remote code execution is the most preferred type of exploit, with 60 vulnerabilities exploited in the wild. The five most prevalent types, comprising over 70% of weaponized vulnerabilities, also included security feature bypass, privilege escalation, buffer manipulation, and input validation and parsing.
Less time to react
The report reveals that network defenders must act with urgency. While the average time to exploit vulnerabilities in 2023 stands at 44 days, in numerous cases, exploits were available on the very same day vulnerabilities were published. The Modus operandi of attackers is shifting, leaving less time for response.
“25 percent of these security vulnerabilities were immediately targeted for exploitation, with the exploit being published on the same day as the vulnerability itself was publicly disclosed,”…




