InfectedSlurs botnet targets QNAP VioStor NVR vulnerability
InfectedSlurs botnet targets QNAP VioStor NVR vulnerability
The Mirai-based botnet InfectedSlurs was spotted targeting QNAP VioStor NVR (Network Video Recorder) devices.
In November, Akamai warned of a new Mirai-based DDoS botnet, named InfectedSlurs, actively exploiting two zero-day vulnerabilities to infect routers and video recorder (NVR) devices.
The researchers discovered the botnet in October 2023, but they believe it has been active since at least 2022. The experts reported the two vulnerabilities to the respective vendors, but they plan to release the fixes in December 2023.
At the time, the company did not reveal the names of the impacted vendors, the researchers determined that the bot also used default admin credentials to install the Mirai variants.
A close look at the ongoing campaign revealed that the bot also targets wireless LAN routers built for hotels and residential applications.
On December 6, The Akamai Security Intelligence Response Team (SIRT) published the first update to the InfectedSlurs advisory series. The security firm revealed that threat actors were exploiting a vulnerability, tracked as CVE-2023-49897 (CVSS score 8.0) that impacted several routers, including Future X Communications (FXC) AE1021 and AE1021PE wall routers, running firmware versions 2.0.9 and earlier.
The Akamai SIRT this week published an additional update after one of the affected vendors, QNAP, released advisory information and guidance.
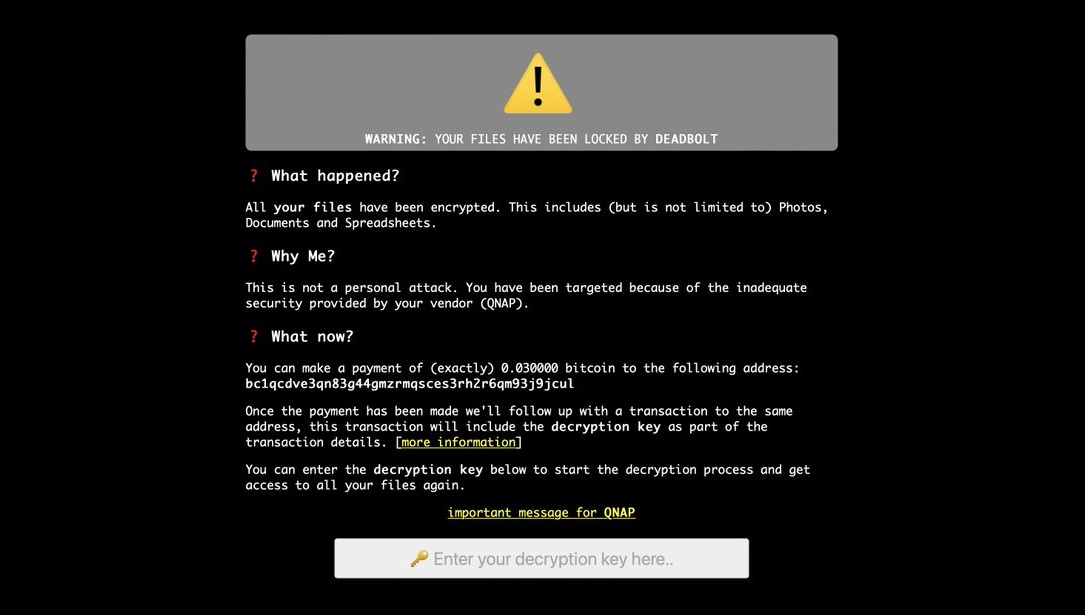
The experts reported that the InfectedSlurs botnet is exploiting a remote code execution (RCE) vulnerability, tracked as CVE-2023-47565 (CVSS score 8.0), in QNAP VioStor NVR (Network Video Recorder) devices.
The vulnerability affects VioStor NVR Versions 5.0.0 and earlier (5.0.0 released June 21, 2014).
“QNAP considers these devices discontinued for support; however, the vendor recommends upgrading VioStor firmware on existing devices to the latest available version. This issue had previously been patched, although it was never publicly reported/disclosed.” reads the advisory published by Akamai.
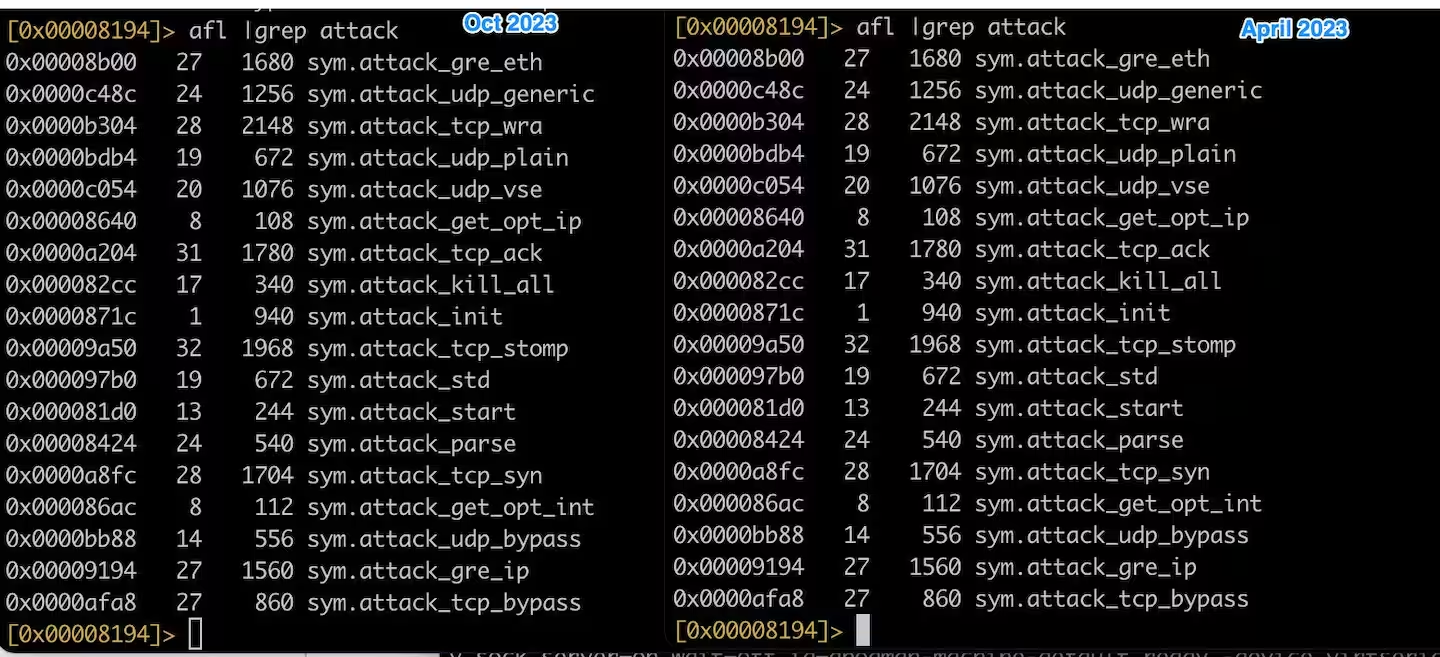
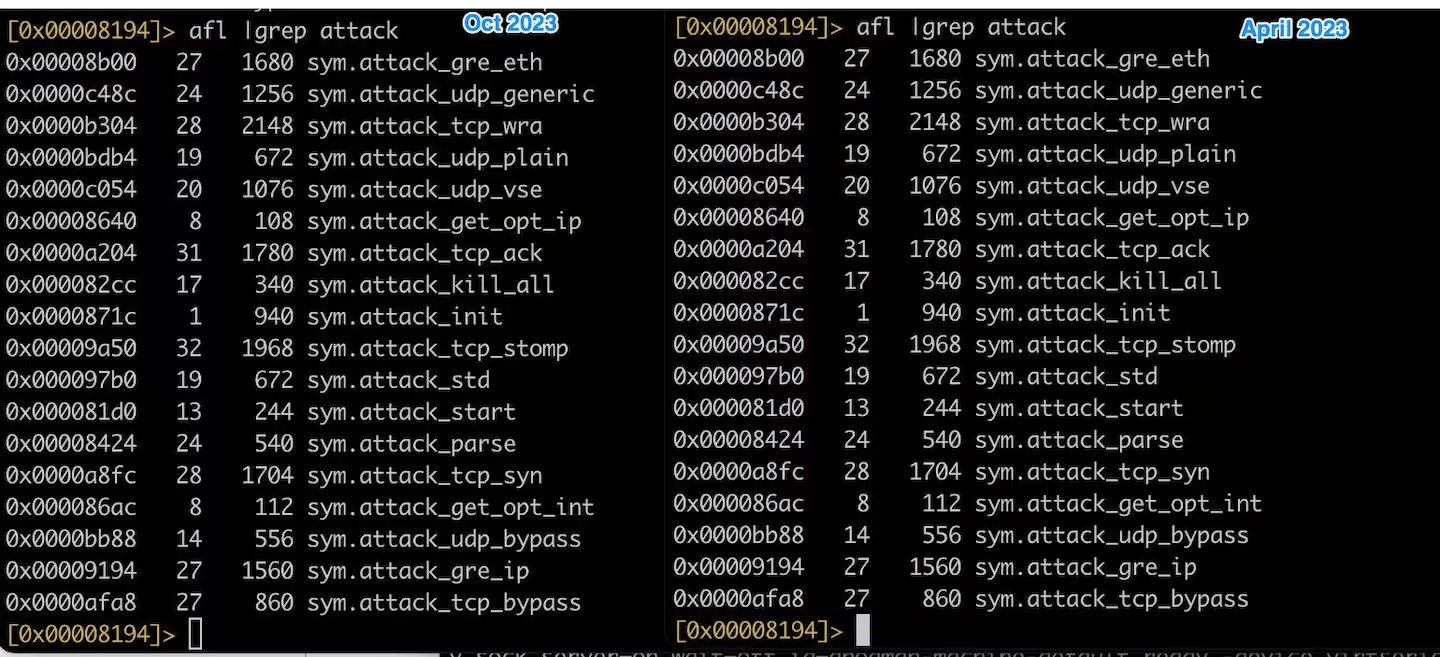
The Akamai SIRT discovered that the bot was running an exploit targeting QNAP VioStor NVR devices…