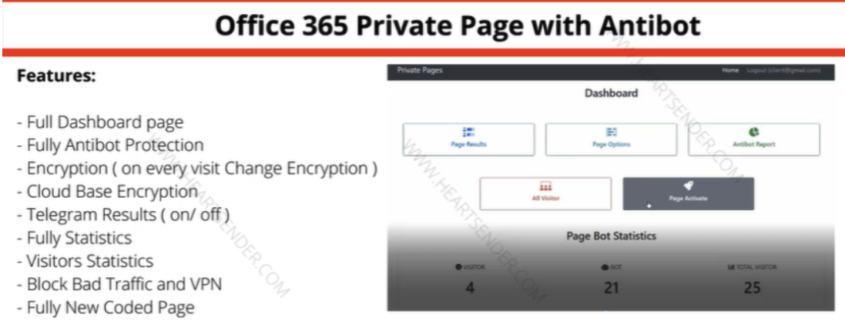
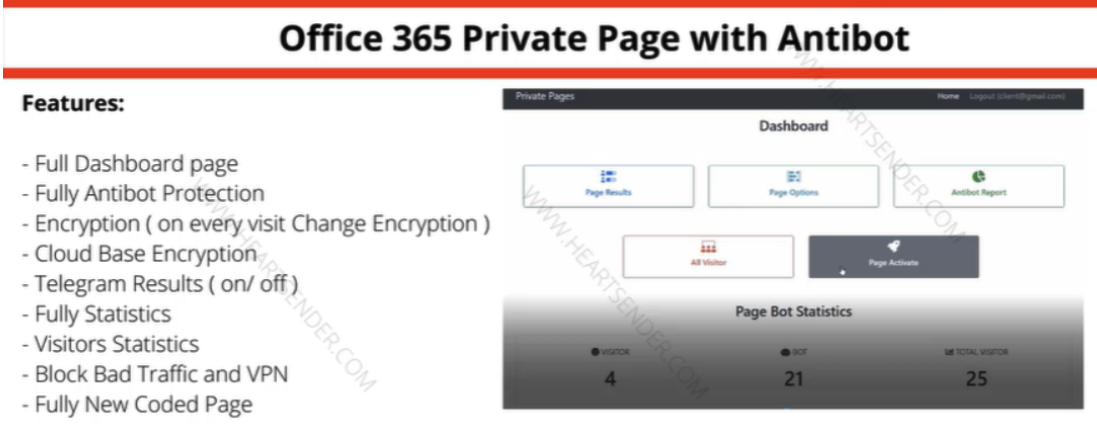
Google releases May 2024 Android security update with Bluetooth improvements and Pixel 8 camera fix
The May update includes enhancements for Bluetooth LE audio stability and performance across most supported Pixel models. It also specifically addresses a camera issue that could cause performance problems in certain video recording scenarios on devices like the Pixel 8 Pro.
The latest updates incorporate security patches from both May 1st and May 5th. The May 1st set of patches primarily addresses various Android Framework and System vulnerabilities. In contrast, the May 5th update focuses on fixes for hardware components from companies like Arm, Qualcomm, and MediaTek. This is the list of fixes according to the changelog:
- General improvements in stability or performance for Bluetooth LE audio
Camera
- Fix for camera performance under certain conditions when recording video
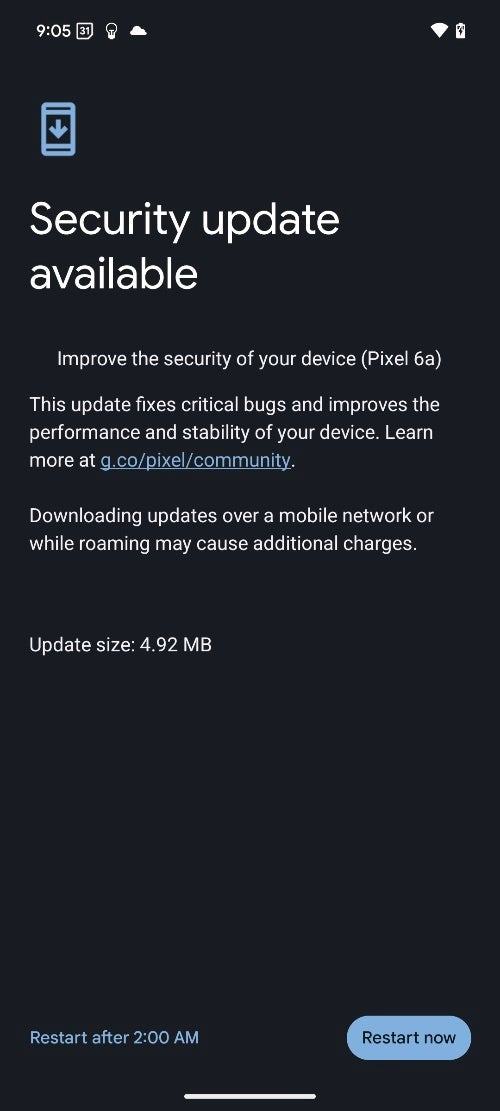

The update is approximately 5MB and the build number varies depending on the device model and carrier. Here is the breakdown on which build number you should expect to receive on your Pixel:
- Pixel 5a (5G): AP1A.240505.004
- Pixel 6: AP1A.240505.004
- Pixel 6 Pro: AP1A.240505.004
- Pixel 6a: AP1A.240505.004
- Pixel 7: AP1A.240505.005
- Pixel 7 Pro: AP1A.240505.005
- Pixel 7a: AP1A.240505.005
- Pixel Tablet: AP1A.240505.004
- Pixel Fold: AP1A.240505.005
- Pixel 8: AP1A.240505.005
- Pixel 8 Pro: AP1A.240505.005
KDDI
- Pixel 7: AP1A.240505.005.B1
- Pixel 7 Pro: AP1A.240505.005.B1
- Pixel 7a: AP1A.240505.005.B1
- Pixel Fold: AP1A.240505.005.B1
- Pixel 8: AP1A.240505.005.B1
- Pixel 8 Pro: AP1A.240505.005.B1
T-Mobile, C Spire, US Cellular & Cellcom
- Pixel 7: AP1A.240505.004
- Pixel 7 Pro: AP1A.240505.004
- Pixel 7a: AP1A.240505.004
- Pixel Fold: AP1A.240505.004
- Pixel 8: AP1A.240505.004
- Pixel 8 Pro: AP1A.240505.004
- Pixel 7: AP1A.240505.005.A1
- Pixel 7 Pro: AP1A.240505.005.A1
- Pixel 7a: AP1A.240505.005.A1
- Pixel Fold: AP1A.240505.005.A1
- Pixel 8: AP1A.240505.005.A1
- Pixel 8 Pro: AP1A.240505.005.A1
To check if your Pixel device has received the May 2024 update, navigate to Settings > System > Software updates > System update….