TeaBot malware slips back into Google Play Store to target US users

The TeaBot banking trojan was spotted once again in Google Play Store where it posed as a QR code app and spread to more than 10,000 devices.
This is a trick that its distributors used before, in January, and even though Google ousted these entries, it appears that the malware can still find a way into the official Android app repository.
According to a report from Cleafy, an online fraud management and prevention company, these applications are acting as droppers. They are submitted without malicious code and request minimal permissions, which makes it hard for Google’s reviewers to spot anything shady.
Also, the trojanized apps include the promised functionality, so user reviews on the Play Store are positive.
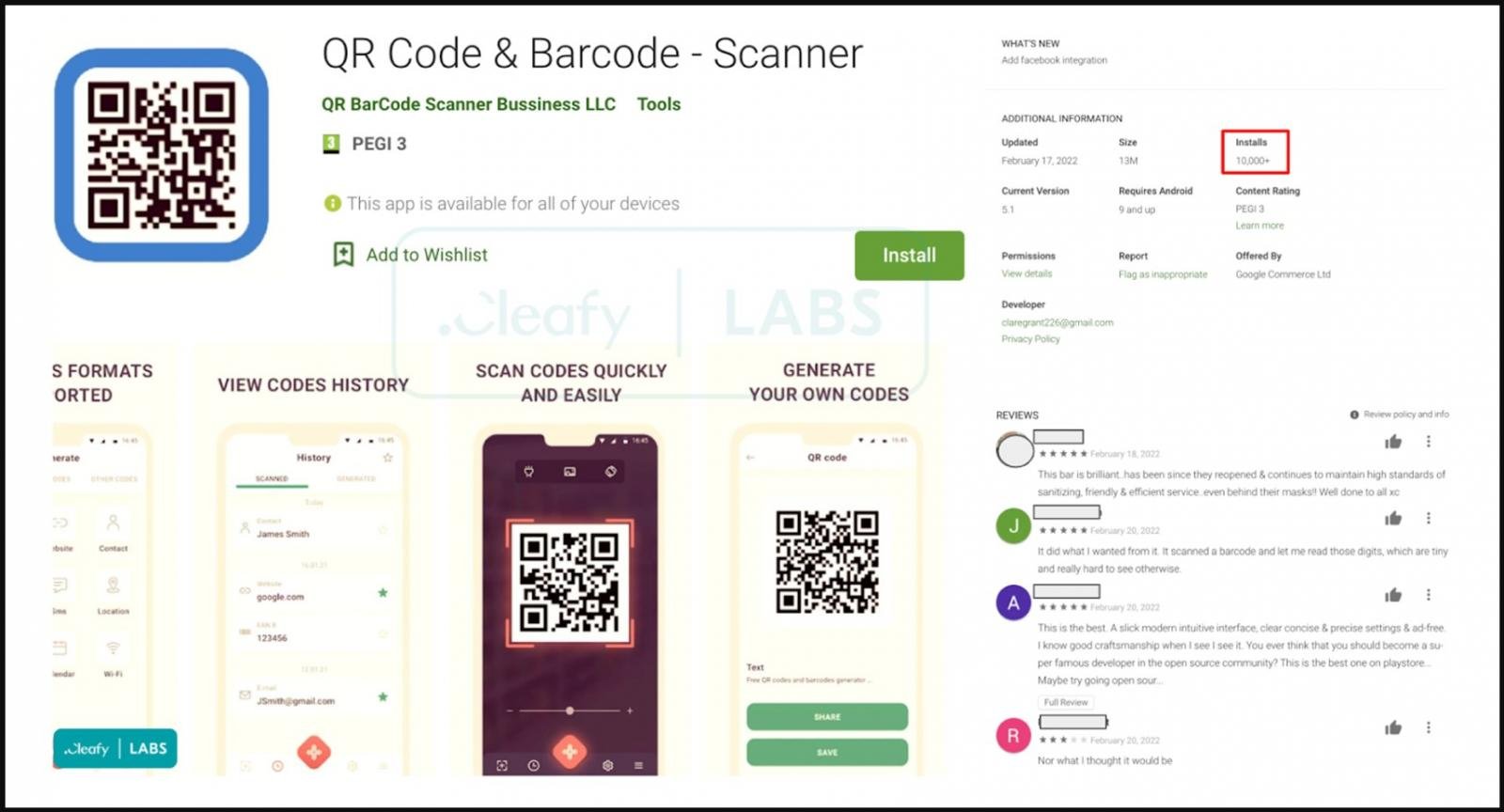
Fetching the TeaBot payload
The In february, researchers found that TeaBot posed as an app named ‘QR Code & Barcode – Scanner’, which appears as a legitimate QR code scanning utility.
Upon installation, the app requests an update through a popup message, but contrary to the standard procedure imposed by the Play Store guidelines, the update is fetched from an external source.
Cleafy traced the download source back to two GitHub repositories belonging to the same user (feleanicusor), containing multiple TeaBot samples, uploaded on February 17, 2022.
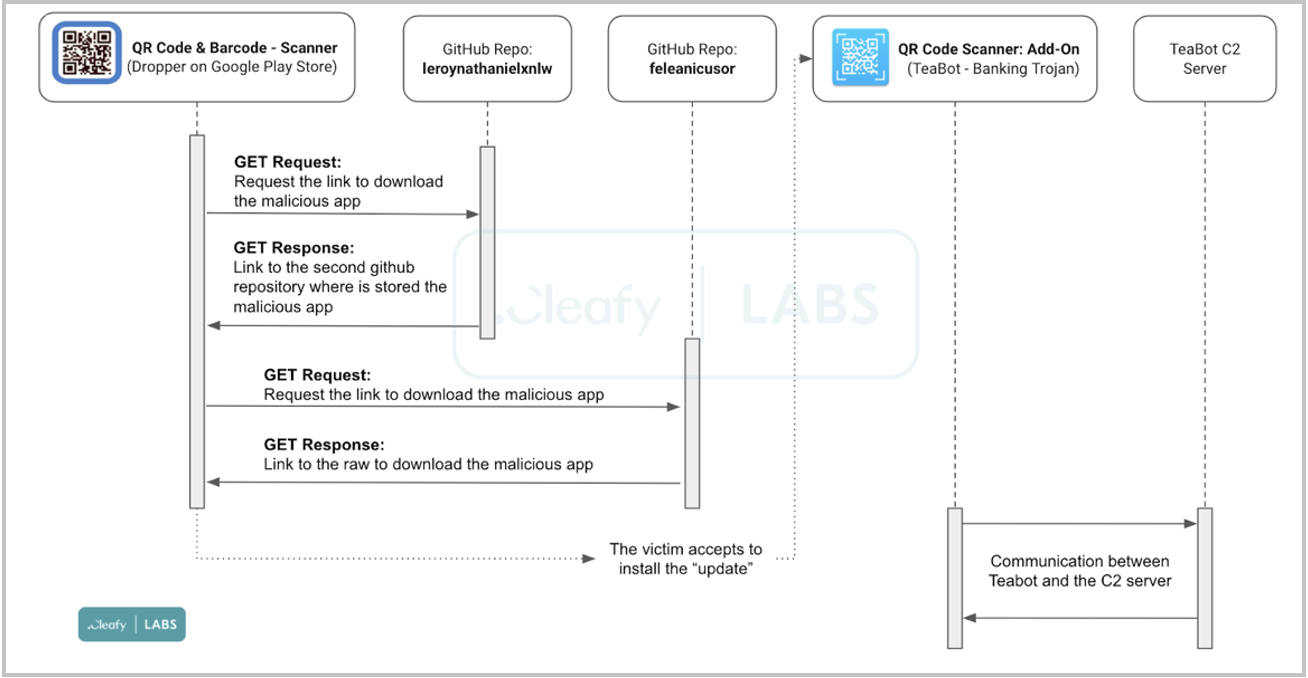
Once the victim accepts to install the update from non-trusted sources, TeaBot is loaded onto their device as a new app under the name ‘QR Code Scanner: Add-On’.
The new app launches automatically and requests the user to grant permission to use the Accessibility Services, to perform the following functions:
- View the device’s screen and grab screenshots that expose login credentials, 2FA codes, SMS content, etc.
- Perform actions such as auto-granting additional permissions in the background without requiring any user interaction.
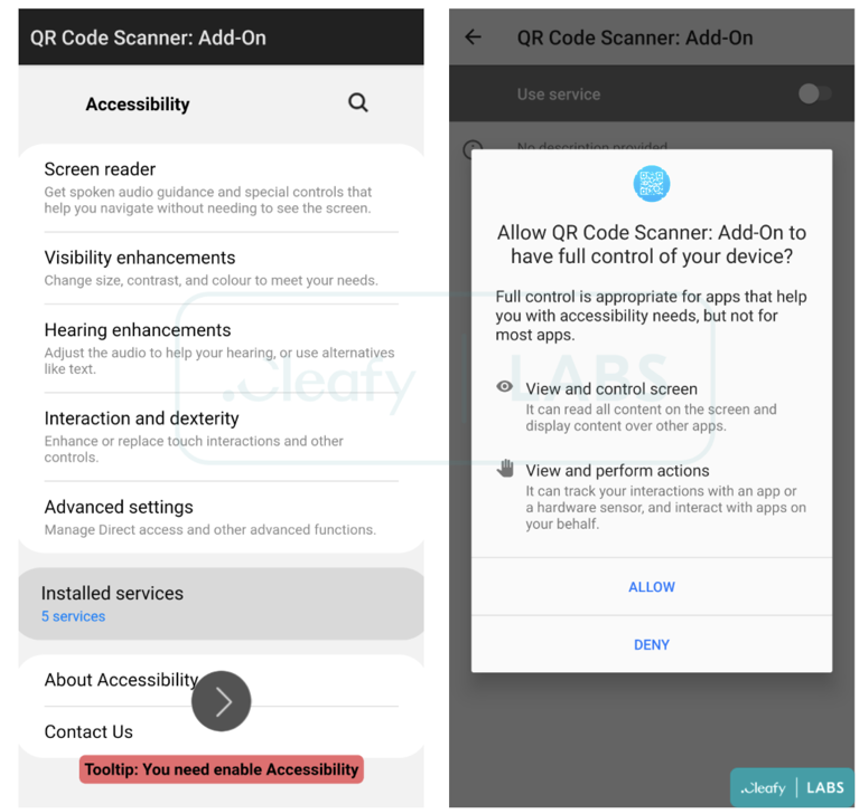
Google has introduced some security-minded API changes for the Accessibility Service in Android 12, but this remains the most commonly abused permission by banking trojans. After all, most Android phones are still running OS version 11 or…