In the dimly lit corridors of digital warfare, a new chapter unfolds as South Korean authorities mount a determined response to a series of cyberattacks that bear the hallmark of a familiar adversary. This isn’t just a skirmish in the nebulous realm of cyberspace; it’s a direct assault on the country’s judicial backbone, compelling the National Police Agency to take unprecedented action against a threat that’s as intangible as it is insidious.
The Frontline: Supreme Court Servers Under Siege
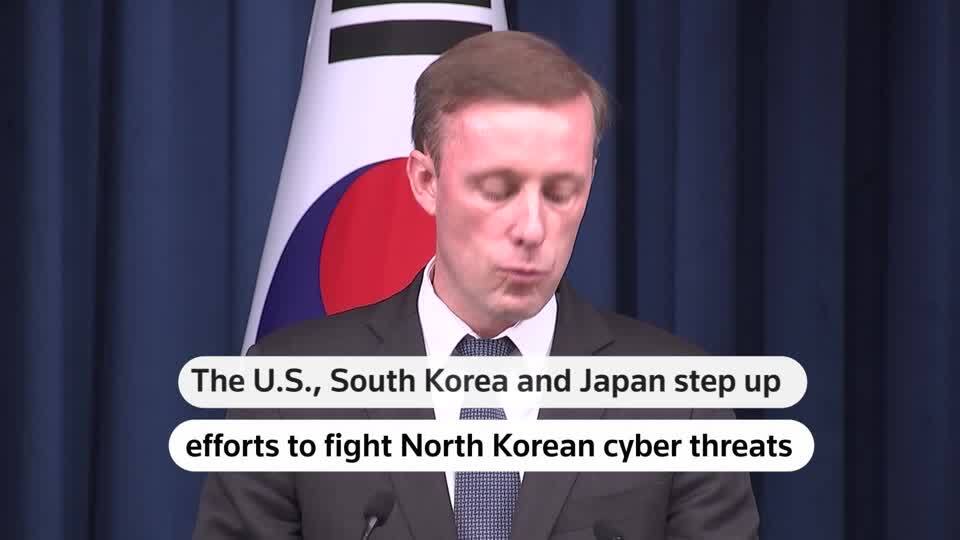
The serene city of Seongnam, merely a stone’s throw from the bustling capital of Seoul, found itself at the epicenter of this cyber confrontation. Here, within the premises of the Supreme Court’s digital data bureau, police initiated search and seizure operations aimed at reclaiming sovereignty over servers that fell victim to the cyberattacks orchestrated by the Lazarus Group, a notorious entity with indelible ties to North Korea. The operations, marking a significant escalation in the fight against cyberterrorism, commenced on February 13th, signaling a clear intent to safeguard national security interests.
A Persistent Threat: The Lazarus Group’s Shadow
The Lazarus Group isn’t a new player on the global stage of cyberterrorism. Known for its sophisticated attacks and elusive operations, this North Korean-affiliated collective has cast a long shadow over international cybersecurity efforts. The breach of the Supreme Court servers is but the latest in a series of provocations that underscore the group’s audacious approach to digital espionage and sabotage. By targeting the judicial system, the attackers not only compromise sensitive legal information but also challenge the very integrity of South Korea’s governance structures.
Securing the Digital Frontier: Response and Repercussions
In response to this brazen incursion, the National Police Agency’s cyber terror division has not only intensified its efforts to recover and secure the compromised servers but also to assess and mitigate the impact of the breach. These efforts are emblematic of a broader struggle to protect critical infrastructure from the increasingly sophisticated…