Hackers Hijack Websites to Inject Malware that Steals Credentials
Concerning a development for internet security, a new form of website malware known as “Angel Drainer” has been increasingly targeting Web3 and cryptocurrency assets since January 2024.
This malware is part of a broader trend of rising Web3 phishing sites and crypto drainers that significantly threaten user credentials and wallets.
Live attack simulation Webinar demonstrates various ways in which account takeover can happen and practices to protect your websites and APIs against ATO attacks
.
Web3 Crypto Malware: Angel Drainer Overview
Angel Drainer is a crypto drainer implicated in security breaches, including a notable incident with Ledger Connect Kit in December.
It operates by injecting itself directly into compromised websites or redirecting visitors to phishing sites containing the drainer. Once in place, it can steal and redistribute assets from compromised wallets, reads the Sucuri report.
The surge in malicious activity is alarming, with over 20,000 unique Web3 phishing sites created in 2023 alone.
As per recent reports, the Angel Drainer phishing group has illicitly acquired a sum of over $400,000 from a total of 128 cryptocurrency wallets.
The group has utilized a new and sophisticated tactic to carry out their fraudulent activities, which is a cause of concern for businesses and individuals alike.
In the first two months of 2024, at least three unrelated malware campaigns have begun using crypto drainers in website hacks.
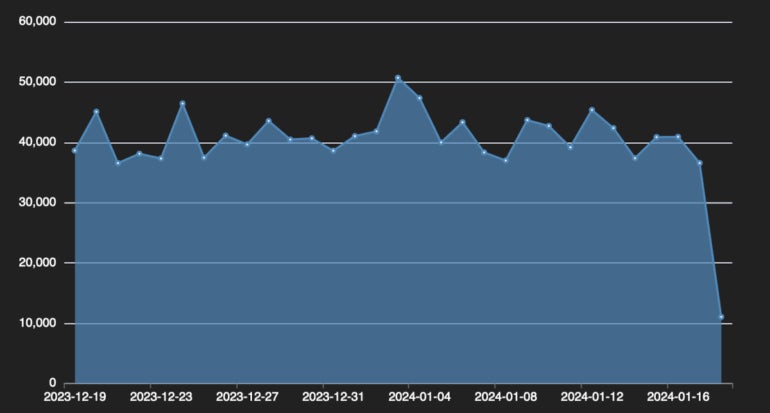
Sucuri’s SiteCheck remote website scanner detected the Angel Drainer variant on over 550 sites since early February, and the public showed this injection on 432 sites at the time of writing.
The impact of these attacks is profound, with Angel Drainer found on 5,751 different unique domains over the past four weeks.
The malware leverages phishing tactics and malicious injections to exploit the Web3 ecosystem’s reliance on direct wallet interactions, endangering both website owners and the safety of user assets.
Injection Methods and Strategies
The injection methods used by these attackers are sophisticated and varied. They can…