94% of Ransomware Victims Have Their Backups Targeted
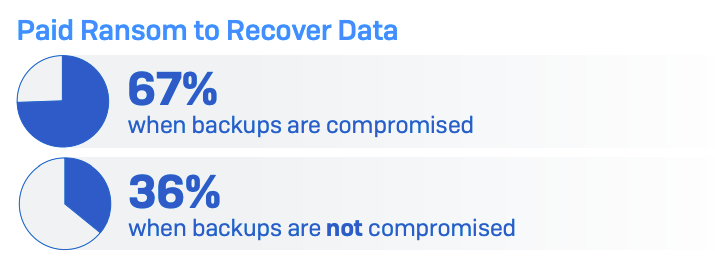
Organisations that have backed up their sensitive data may believe they are relatively safe from ransomware attacks; however, this is not the case based on findings from a new study from IT security company Sophos. The report showed that cybercriminals attempted to compromise the backups of 94% of companies hit by ransomware in the past year.
Attackers are aware that those who fall victim to ransomware must choose to either pay the ransom or recover their now-encrypted systems from a backup. To put more pressure on decision-makers to pay up, it is becoming more common for them to target the duplicated data as well as the production data. Indeed, the report showed the victim is almost twice as likely to pay up if their backup is compromised, and recovery from the attack is eight times more expensive.
The Sophos research revealed the extent of the popularity and effectiveness of ransomware groups targeting corporate backups (Figure A).
Figure A
SEE: What is ransomware? Read this TechRepublic cheat sheet
How much does it cost to recover from a ransomware attack on the backup?
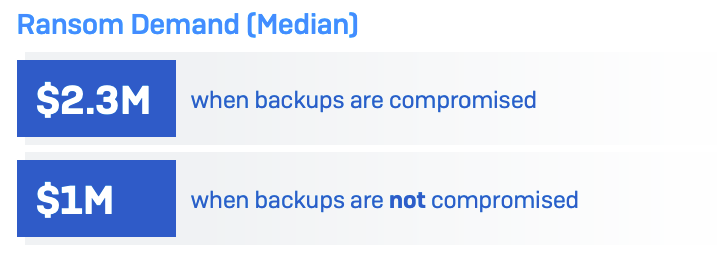
The Sophos research found that the median ransom demand for organisations whose backups are compromised is $2.3 million (£1.8 million) (Figure B). When the backup is not compromised, the median ransom demand is $1 million (£790k), as the attacker has less leverage.
Figure B
“Ransomware-led outages frequently have a considerable impact on day-to-day business transactions while the task of restoring IT systems is often complex and expensive,” Sally Adam, the senior director of marketing at Sophos, wrote in the report.
Companies without compromised backups are also more likely to be able to negotiate the ransom payment down, paying out an average of 82% of the initial demand. Those whose backups are compromised will pay 98% of the demanded sum, on average.
The total cost of a ransomware attack is often more than just the ransom, as it incorporates the…