Trust Wallet Warns About iOS Zero-Day Exploit

Popular crypto wallet provider Trust Wallet disclosed on April 15 that it received “credible intel” about a high-risk zero-day exploit being sold on the Dark Web to target iOS users.
According to the software developer, this flaw could allow hackers to gain unauthorized access to users’ personal data.
Trust Wallet Reports Personal Information Sale on Dark Web
Trust Wallet shared its discovery in an X post, explaining the dangers of the zero-day exploit targeted at iMessage.
1/2: ⚠️ Alert for iOS users: We have credible intel regarding a high-risk zero-day exploit targeting iMessage on the Dark Web.
This can infiltrate your iPhone without clicking any link. High-value targets are likely. Each use raises detection risk. #CyberSecurity
— Trust Wallet (@TrustWallet) April 15, 2024
A zero-day exploit is a cyber attack that takes advantage of a previously unknown vulnerability in software. These exploits can go undetected for an extended period and are used to gain unauthorized access to systems and steal data. As detailed in the X post, iOS users and the entire crypto ecosystem could be at risk.
Trust Wallet CEO Eowyn Chen also shared a screenshot on X that reportedly depicts a zero-day exploit for sale on the Dark Web for $2 million.
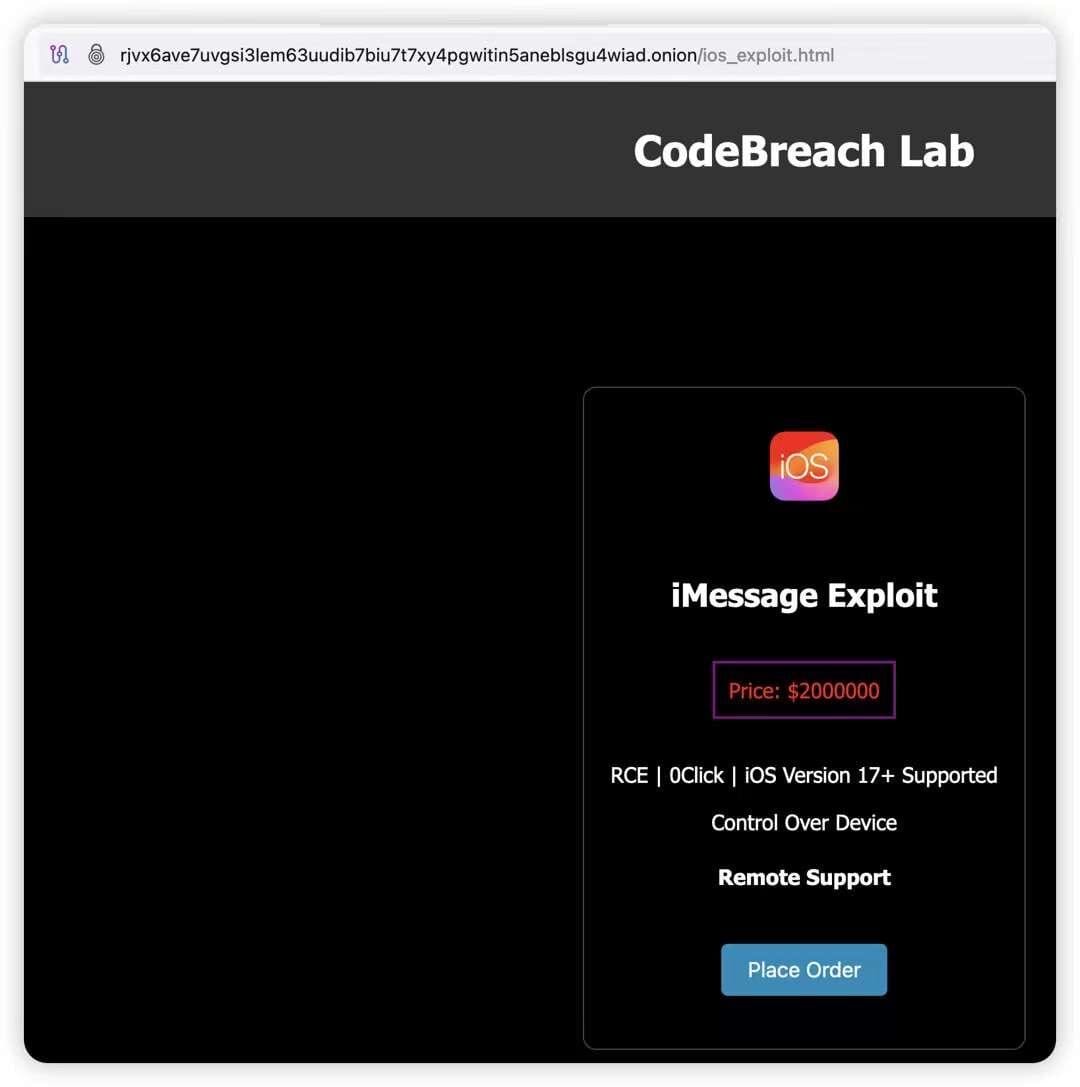
Neither the crypto wallet provider nor its CEO disclosed where this information came from or if there were any casualties, however.
Due to this post getting a lot of views & comments, we thought we’d elaborate further for the community:
How did we come by this intel?
Trust Wallet is constantly monitoring multiple avenues for any and all security…





