As Internet Usage Grows, Californians Are Concerned about Online Security
The onset of the pandemic made internet access increasingly central to daily life—in 2021, a record-high 85% of Californians were using the internet at home. Given the wide range of internet activity, online privacy and security are key issues. What can the latest data from the National Telecommunications and Information Administration’s 2021 Internet Use Survey tell us about Californians’ internet usage and security concerns?
The internet has become an important conduit for a wide range of daily activity. Californians are most likely to use the internet to connect with others. However, more than half (56%) access health records or insurance information online, and nearly half use online government services. Notably, about one in four Californians search or apply for jobs online, while 27% participate in online classes or job training and 31% telecommute.
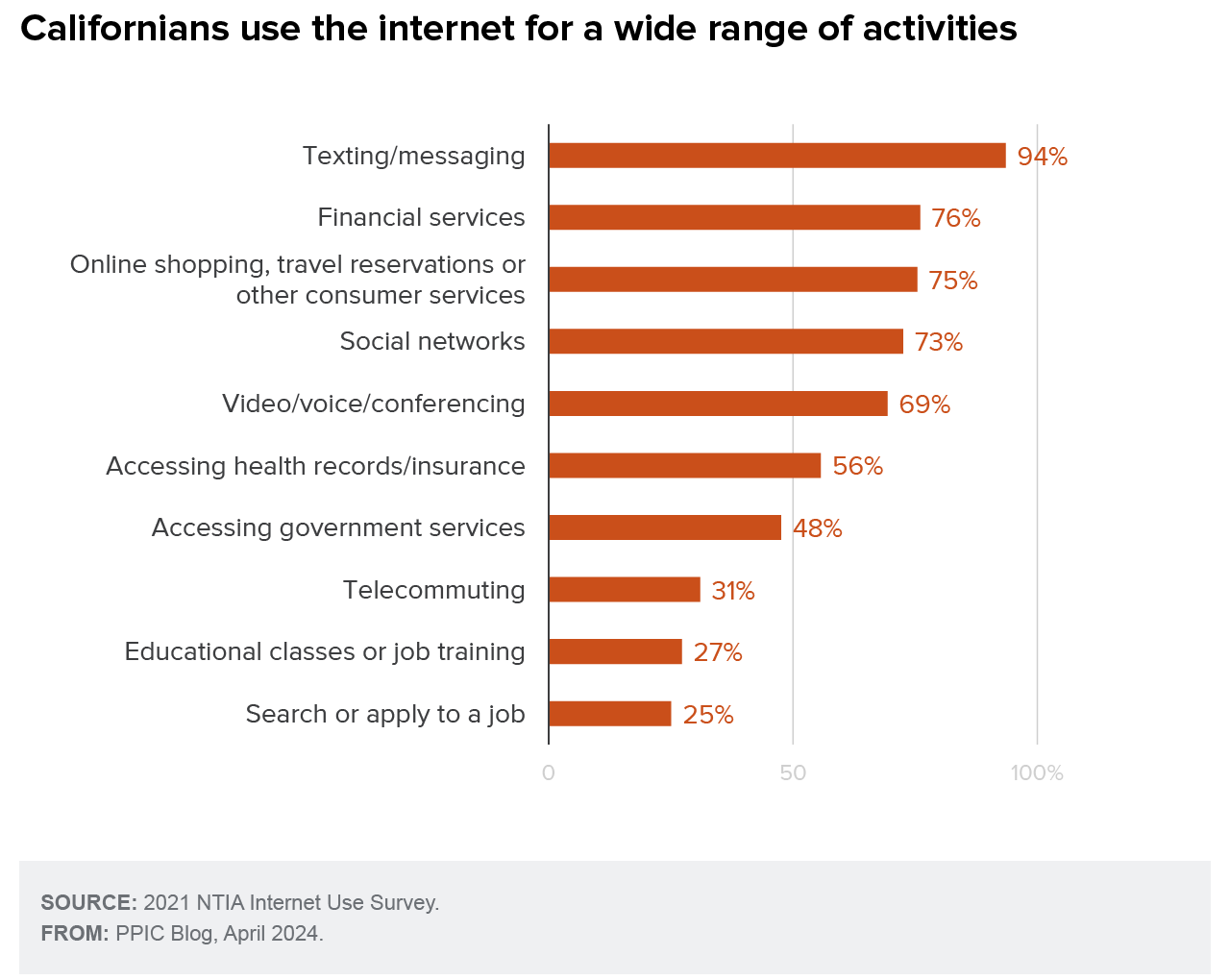
High-income households (those earning more than $100,000 per year) are more likely than lower-income households to use the internet across all of these domains. Gaps in usage are especially notable when it comes to accessing government services, financial services, and health records, with nearly 60% of high-income households going online for government services, compared to 33% of low-income households. Black, Latino, and households headed by people without a bachelor’s degree are also less likely to access government services online. These disparities are often attributed to gaps in digital access and literacy.
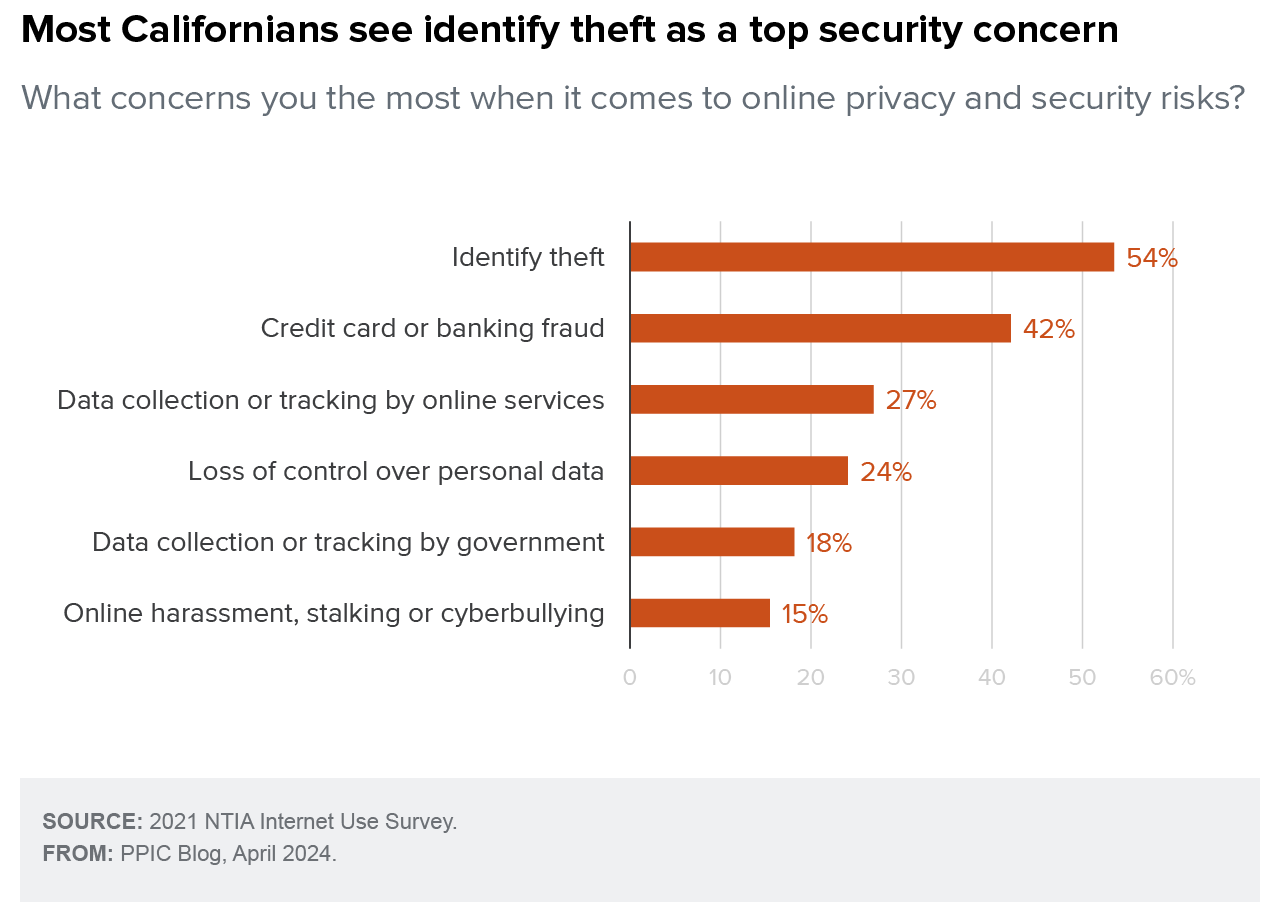
While internet usage is widespread, privacy and security concerns have deterred many people from engaging in economic and civic activities online. Californians tend to be most concerned about identify theft (54%), but many are worried about credit card or banking fraud (42%), data tracking by online services (27%) and loss of control over their personal data (24%).
There is good reason for these concerns. About one in five Californians have been affected by an online security breach, identify theft, or similar crime. High-income households (25%) and Black and white households (25% and 24% respectively) households are especially likely to be affected by privacy or security breaches.
Now that…



