Trend Micro Dissects Big Head Ransomware Variants Currently Making The Rounds
Earlier this year, reports of a new ransomware family dubbed ‘Big Head’ appeared online in various malware databases. This malware is making the rounds through malvertisement campaigns that look like Windows updates and Word installers, which is rather concerning becuase less savvy users often fall for these attacks.
Researchers at Trend Micro began to dig into this malware as it and three variants were discovered, and have published a technical report on the samples. The first sample is a .NET compiled binary that drops three subsequent executables, 1.exe, Archive.exe, and Xarch.exe, which all have different purposes.
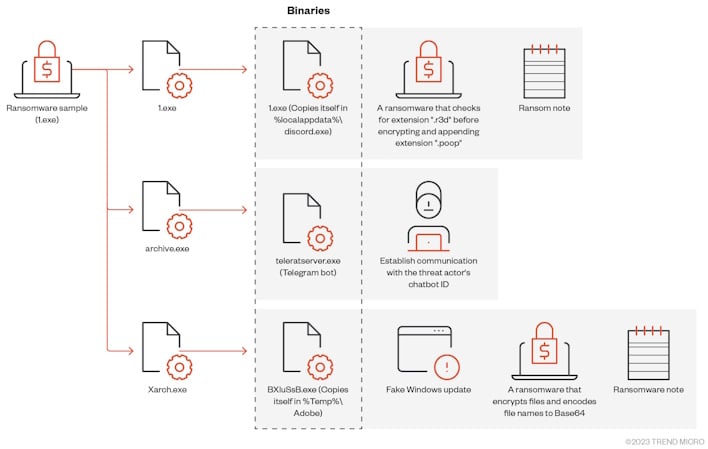
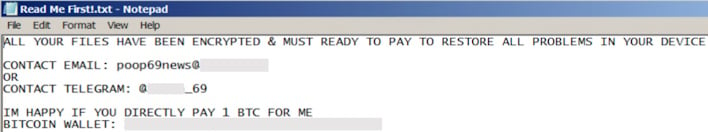
1.exe embeds itself on the system, encrypts files with the ‘.poop’ extension, creates the ransom note, and changes the victim’s desktop background. Archive.exe drops another executable, a Telegram tool that establishes a line of communication with the threat actor to execute remote activities. Xarch.exe finally drops BXluSsB.exe, another ransomware that encrypts files and displays a fake Windows update to make the malicious activity seem legitimate.
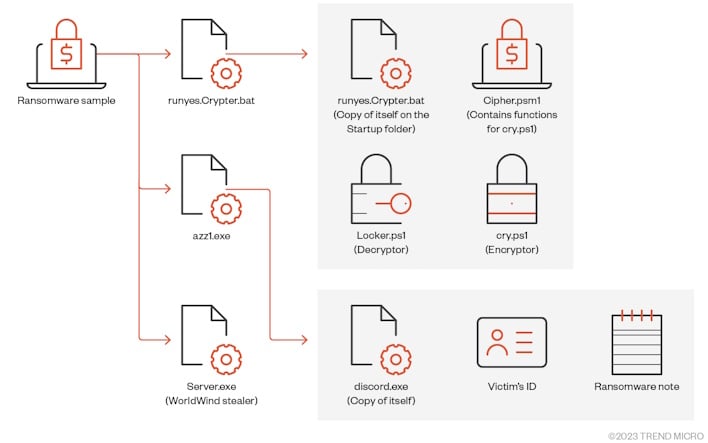
The second sample has similar activity, but substitutes an extra ransomware binary for an information stealer binary. This malware, identified as the WorldWind stealer, will grab browsing history, directory listings, running processes, product keys, network connections, and screenshots, all of which are likely exfiltrated to the threat actor’s Telegram.
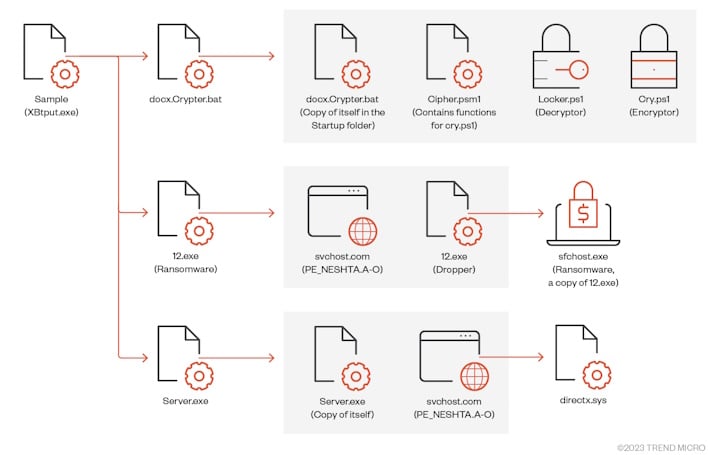
The third and final sample includes Neshta, a virus “designed to infect and insert its malicious code into executable files.” The researchers believe that this is a diversion technique to prevent tools designed to detect ransomware from triggering. It is also noted that with this sample, the ransom note and wallpaper are different from previous samples but contain similar information.
Though there are notable differences between all of the analyzed samples, the researchers at Trend Micro suspect that all of them come from the same malware developer. Trend thinks this is the case because the samples have similar routines or structures in their infection process, have the same email and Telegram accounts, and have other similar mistakes in the malware…