Researchers Explore Hacking VirusTotal to Find Stolen Credentials
Security researchers have found a method to collect vast amounts of stolen user credentials by executing searches on VirusTotal, the online service used to analyze suspicious files and URLs.
With a €600 (around $679) VirusTotal license and a few tools, the SafeBreach research team collected more than a million credentials using this technique. The goal was to identify the data a criminal could gather with a license for VirusTotal, which is owned by Google and provides a free service that can be used to upload and check suspicious files and links using several antivirus engines.
A licensed user on VirusTotal can query the service’s dataset with a combination of queries for file type, file name, submitted data, country, and file content, among others. The SafeBreach team created the idea of “VirusTotal hacking” based on the method of “Google hacking,” which criminals use to look for vulnerable websites, Internet of Things devices, Web shells, and sensitive data leaks.
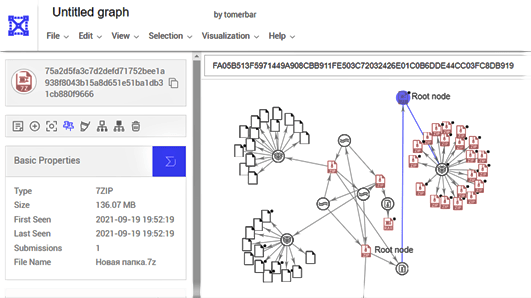
Many information stealers collect credentials from different forums, mail accounts, browsers, and other sources, and write them to a fixed hard-coded file name — for example, “all_credentials.txt” — then exfiltrate this file from the victim’s device to the attackers’ command-and-control server. Using this method, researchers took VirusTotal tools and APIs such as search, VirusTotal Graph, and Retrohunt, and used them to find files containing stolen data.
“It is quite a straightforward technique, which doesn’t require strong understanding in malware,” says Tomer Bar, director of security research at SafeBreach. “All you need is to choose one of the most common info stealers and read about it online.”
The researchers conducted their research using known malware including RedLine Stealer, Azorult, Raccoon Stealer, and Hawkeye as well as known forums such as DrDark and Snatch_Cloud to steal sensitive data. They found their method works at scale.
RedLine Stealer is a form of malware sold on underground forums via a stand-alone purchase or subscription. It uses browsers to collect data such as saved credentials, autocomplete data, and credit card details. When it runs on a target machine, the malware takes a…