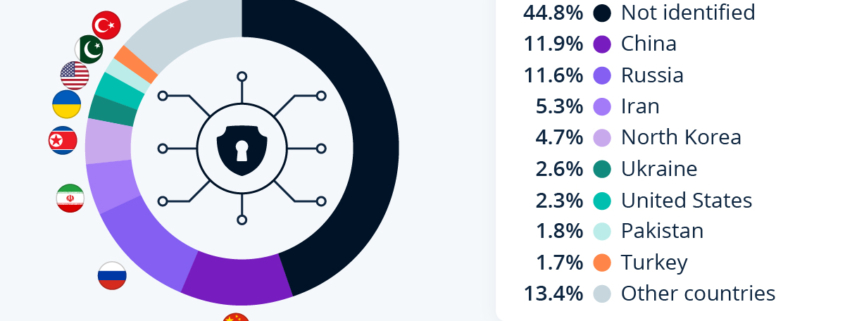
Chart: Who’s Behind Cyber Attacks?
The Cybersecurity and Infrastructure Security Agency (CISA), alongside the National Security Agency (NSA) and the Federal Bureau of Investigation (FBI), has issued a warning about potential cyber threats posed by Chinese state-sponsored actors targeting critical infrastructure in the United States.
The warning follows recent incidents involving a group known as Volt Typhoon, which also goes by names such as Vanguard Panda and BRONZE SILHOUETTE, and is believed to have breached the IT environments of multiple critical infrastructure organizations in the U.S., including in Communications, Energy, Transportation Systems, and Water and Wastewater Systems sectors. According to the advisory, these malicious actors are actively attempting to infiltrate U.S. networks and are potentially paving the way for disruptive or destructive cyberattacks.
Between 2000 and 2023, the European Repository of Cyber Incidents (EuRepoC) database recorded a total of 2,506 politically motivated cyber attacks worldwide, perpetrated by 679 known actors/groups. These cyber incidents include politicized and non-politicized attacks aimed at political targets, as well as attacks against critical infrastructure, whether carried out by states (and affiliated groups) or by non-state actors with political objectives.
As detailed in the following infographic, almost 12 percent of politically-motivated cyberattacks detected since the turn of the century were launched from China, followed by Russia with a similar share (11.6 percent). Iran was responsible for 5.3 percent of these cyber incidents over the period studied, and North Korea for 4.7 percent. It’s important to note here that most malicious acts of this type (45 percent) were unattributed, meaning that the country of origin could not be identified in many cases.
Almost a third of the politically-motivated cyber attacks analyzed were carried out by states (or affiliated groups), and a similar proportion by non-state actors with political objectives. Around half of the attacks recorded were aimed at political targets (public figures, political parties, etc.), and almost 20 percent at critical infrastructures.